ENISA’s Threat Landscape Report 2022 – Part 7 – DDoS attacks

One of the most significant threats to IT systems is Distributed Denial of Service (DDoS), which aims to compromise system availability by depleting resources, resulting in decreased performance, data loss, and service outages. In recent times, DDoS attacks have expanded to mobile and sensor-based scenarios, which can drain battery life, leading to reduced device and sensor availability. Despite remaining largely unchanged over the years, the evolution of DDoS attacks has revealed some interesting aspects.
Despite the strengthening of defense mechanisms and strategies, attackers are continually developing and adapting new techniques to overcome them. These tactics include the use of server-class botnets, DDoS-for-Hire services, and the growing prevalence of direct-path attacks. This ongoing evolution of the threat landscape is perpetuated by the attackers’ constant drive to innovate and find new vulnerabilities to exploit.
In 2021, the size of DDoS attacks saw a significant increase, with several attacks reaching Tbps levels. Analysis of the attack frequency by size revealed a preference for attacks between 1 and 3 Gbps over smaller attacks, and attacks between 10 and 30 Gbps over those between 6 and 10 Gbps. The number of application attacks increased by 2.2%, while protocol attacks rose by 4.7%, with a corresponding decrease in volumetric attacks by 6.9%. This increase in complexity highlights the difficulty of defending against protocol and application attacks, which can mimic genuine application traffic. These types of attacks contributed to the rise in TCP-based attacks, which are essential for targeting complex protocols and applications.
In the past year, multi-vectored attacks were more frequent than single-vectored attacks and are now prevalent.
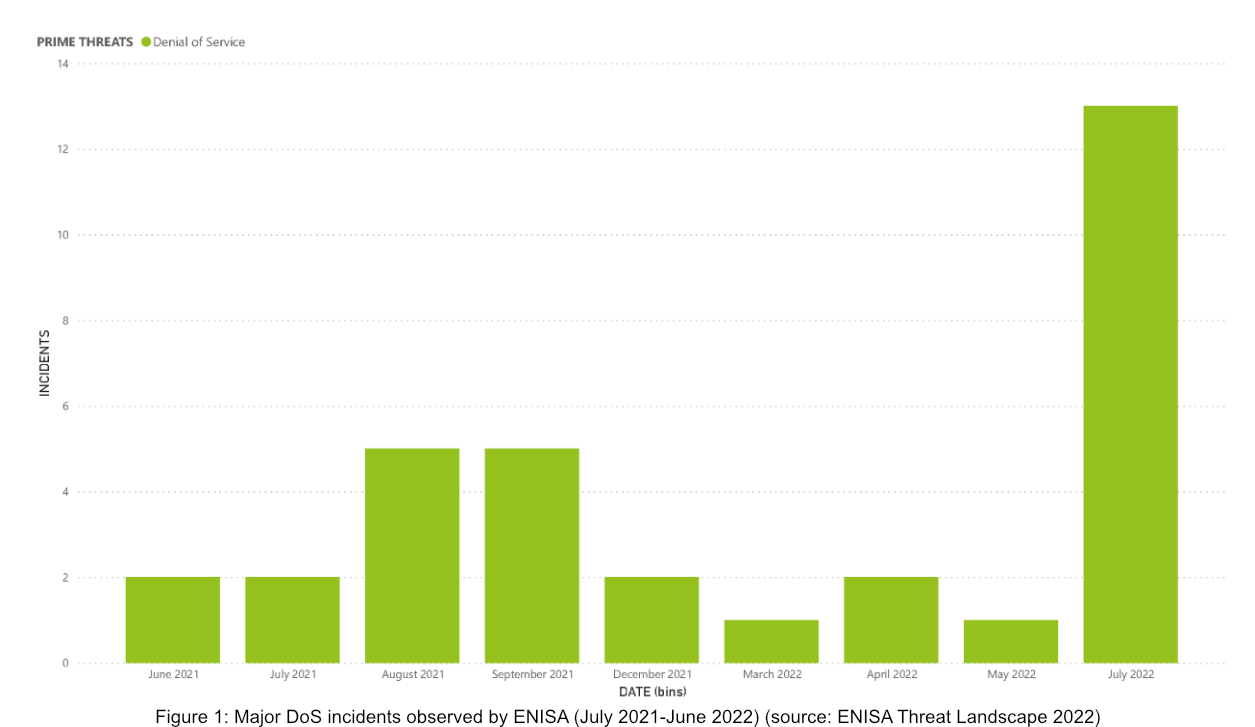
During the period covered by the report, numerous Denial of Service incidents were observed, with a significant increase noted in July 2022. This month saw the largest recorded attack against a European customer on the Prolexic platform, which utilized globally distributed attack traffic and reached a peak of 853.7 Gbps and 659.6 Mbps over 14 hours.
DDoS attacks, mobile networks & IoT
DDoS attacks are shifting from traditional targets toward mobile networks and IoT. Devices and sensors, which often have limited resources and weak security protection, are particularly vulnerable to these attacks. With the increasing complexity of mobile systems, users’ lack of security skills becomes even more relevant. DDoS attacks aim to threaten the availability of components, disrupt the operation of other networks or systems, and potentially threaten user safety. The growing number of devices and applications connected to the cloud provides attackers with a broader range of targets.
Compromised servers and consumer devices such as IoT products and broadband routers have been frequently used to launch DDoS attacks. This is often due to smart device owners delaying updates and patches. For example, the Mozi Botnet still exploits vulnerabilities that were discovered eight years ago and compromises unpatched devices to build botnets with hundreds of thousands of bots. An experiment conducted by the US National Institute of Standards and Technology (NIST) confirmed that “admin” and “1234” were the most commonly used username and password combinations in attacks against IoT.
Ransom Denial of Service (RDoS)
Ransom Denial of Service (RDoS) represents the latest trend in denial-of-service attacks. It targets vulnerable systems and engages in various activities to coerce victims into paying a ransom.
There are two types of RDoS:
- attack-first – a DDoS attack is implemented and a ransom is requested to stop it.
- extortion – an extortion letter and proof in the form of a small-scale DoS is sent with a request to pay a ransom.
Ransom Denial of Service (RDoS) attacks are particularly hazardous because they can be executed even if the attacker lacks sufficient resources. These attacks are intricate and involve a combination of techniques and approaches, such as Denial of Service, identity spoofing, Ransomware, and more.
Ransom Denial of Service (RDoS) attacks have been observed targeting ISPs, financial institutions, and small to medium-sized businesses (SMBs) due to the proliferation of online services. These attacks have been successful due to the adoption of double-extortion methods, where the attacker exfiltrates victim data and threatens to publish it. Furthermore, an expansion of target boundaries involving clients, business partners, and employees of the victim has been noted, leading to the use of triple and quadruple extortion tactics. In triple-extortion tactics, the threat actors encrypt and steal data and also threaten to launch a distributed denial of service (DDoS) attack against the affected organisation. In quadruple-extortion attacks, ransomware cybercriminals escalate the scope of the attack to business partners and clients to increase pressure on the victim, which can lead to business disruptions caused by the ransomware attack.
A further step in RDoS attacks involves requesting a daily payment of 1 BTC in exchange for the attacker’s promise to protect the targeted company from future attacks.
DDoS and the Cloud
The widespread adoption of cloud computing and its shift towards edge computing has expanded the attack surface and created more opportunities for cybercriminals. This migration has been accelerated by factors such as remote work, online education, business resilience, and environmental sustainability resulting from the COVID-19 pandemic. However, this convenience comes at the cost of an increased risk of DDoS attacks targeting cloud resources. Unfortunately, cloud computing often creates a false sense of security, leading to reduced efforts by organizations to monitor cloud infrastructures and platforms compared to their on-premises counterparts. Consequently, cybercriminals are targeting cloud services, exploiting weaknesses in cloud assets and configuration management.
Moreover, cloud computing provides cybercriminals with a powerful tool that offers highly scalable and dependable command-and-control infrastructures and botnets. Additionally, public APIs can be exploited as attack vectors to gain entry to individual endpoint devices.
The Russian war in Ukraine
The cyber warfare between Russia and Ukraine has greatly impacted the evolution of DDoS attacks, with both sides being subjected to significant attacks. The attacks involved various actors, ranging from states to individual users contributing their resources to the cyber war. It’s worth noting that state-sponsored attacks weren’t solely tied to the war but were present before the conflict began. DDoS threats are now being recognized as the fifth dimension of warfare, following battles in the air, sea, land, and space.
DDoS attacks by Industry
The banking, financial services, and insurance (BFSI) sector was the most targeted industry sector, accounting for more than 25% of the attacks. The telecommunications and technology sectors ranked second and fourth, respectively, while the education sector remained a popular target, ranking third.
Attack vectors and technology
Volumetric attacks were the most frequent type of DDoS attacks observed, comprising 59% of all attacks, while application and protocol attacks were the second most common.
In terms of technology, TCP was used in 27% of attacks, representing a 10% increase from the previous period. This increase is closely related to the rise of complex protocol and application DDoS attacks, which often rely on the TCP protocol as a foundation.





0 Comments