Threat Sources, Vulnerabilities, and Incidents – part 2

System Vulnerabilities and Predisposing Conditions
Security controls must provide clear identification of the systems they apply to. These systems can vary greatly in size, scope, and capability. On the smaller end, a system could refer to an individual hardware or software product or service. On the larger end, we encounter complex systems, systems-of-systems, and networks that incorporate hardware architecture and software frameworks, including application frameworks, to support operations. To effectively apply security controls, an organization may choose to designate security zones that encompass all systems within them.
The vulnerabilities within a system can arise from its hardware, firmware, and software components. These vulnerabilities may stem from design flaws, development flaws, misconfigurations, inadequate maintenance, poor administration, or connections with other systems and networks. The SP 800-53 and the OT overlay contain numerous controls that address these vulnerabilities.
Additionally, auxiliary components supporting OT systems can also possess vulnerabilities. This section focuses on a subset of vulnerabilities that have the potential to impact the physical processes.
To summarize, the potential vulnerabilities and predisposing conditions commonly found in OT systems can be categorized into the following groups:
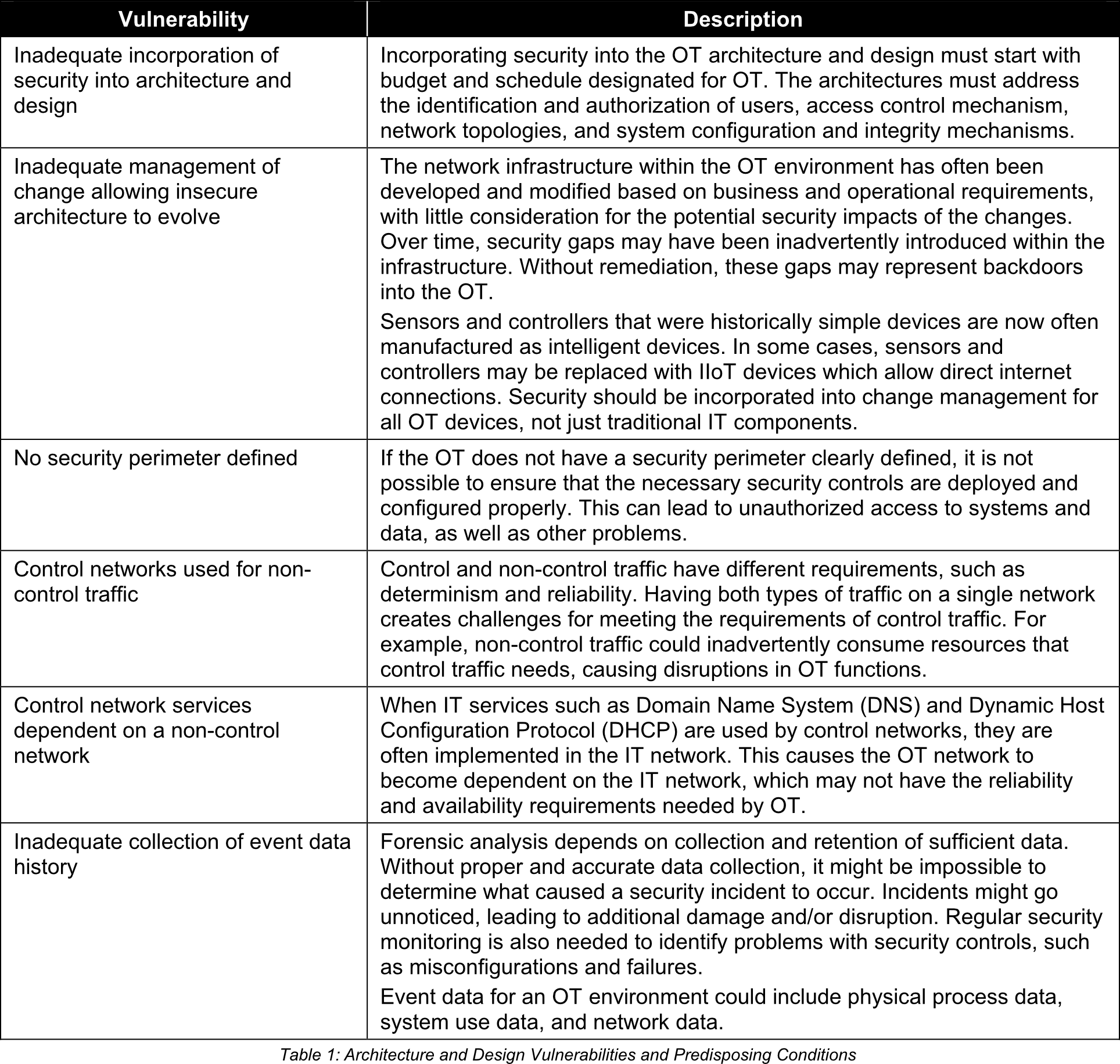
1. Architecture and Design Vulnerabilities and Predisposing Conditions
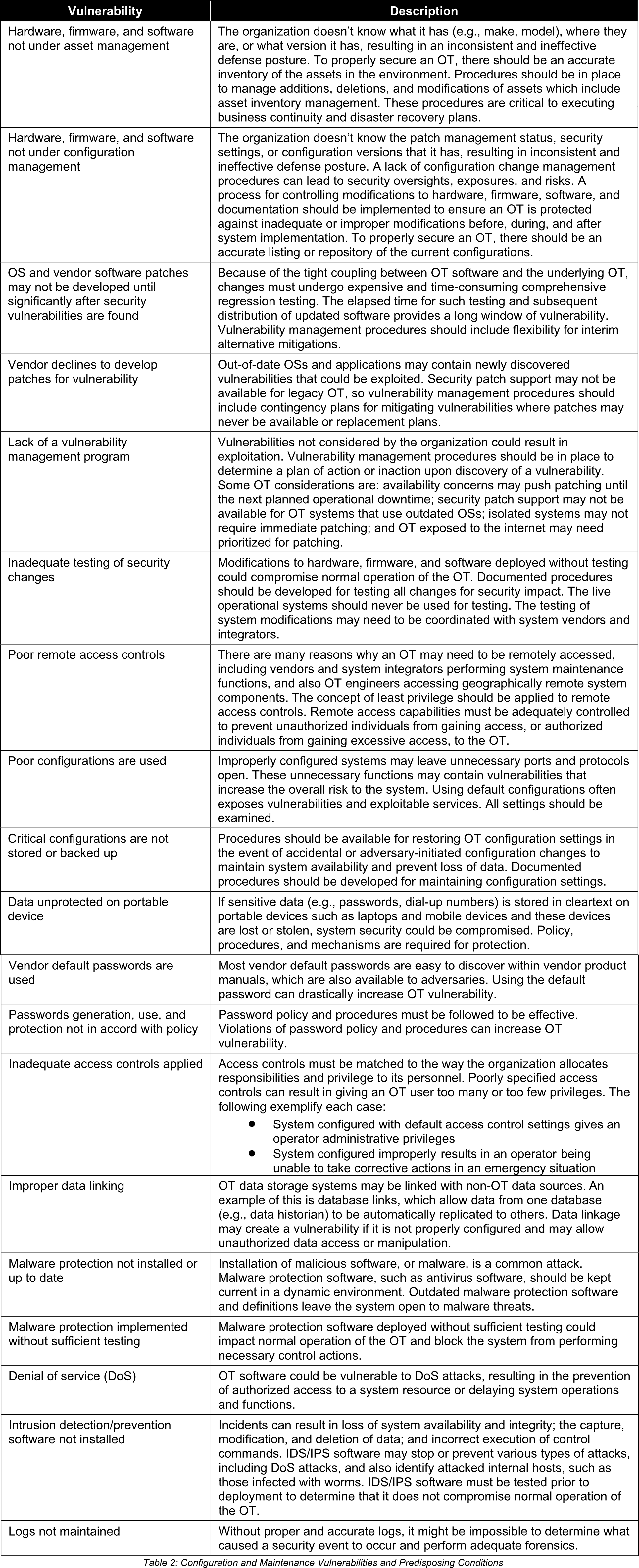
2. Configuration and Maintenance Vulnerabilities and Predisposing Conditions
3. Physical Vulnerabilities and Predisposing Conditions
4. Software Development Vulnerabilities and Predisposing Conditions
5. Communication and Network Configuration Vulnerabilities and Predisposing Conditions
6. Sensor, Final Element, and Asset Management Vulnerabilities and Predisposing Conditions
Architecture and Design Vulnerabilities and Predisposing Conditions
Configuration and Maintenance Vulnerabilities and Predisposing Conditions
To read about the remaining system vulnerabilities categories and their predisposing conditions return to our blog next week.




0 Comments