ENISA’s Threat Landscape Report 2022 – Part 3 – Ransomware

In the 2022 report, ENISA’s Threat Landscape for Ransomware Attacks, ransomware is defined as an attack where the threat actors take control of someone’s assets and demand a ransom in exchange for giving back access to those assets. The report covers the three key elements that are present in every ransomware attack, which are assets, actions, and blackmail. This definition is action-agnostic, which means that it covers the changing ransomware threat landscape, multiple extortion techniques, and different goals, besides just financial gains. Furthermore, the report discusses the four high-level actions used by ransomware to impact the assets’ availability, confidentiality, and integrity, which are lock, encrypt, delete, and steal.
Throughout this reporting period, we have once again witnessed a substantial number of incidents involving ransomware, providing further evidence that the threat posed by ransomware continues to expand. The analysed incidents primarily concentrate on European Union countries.
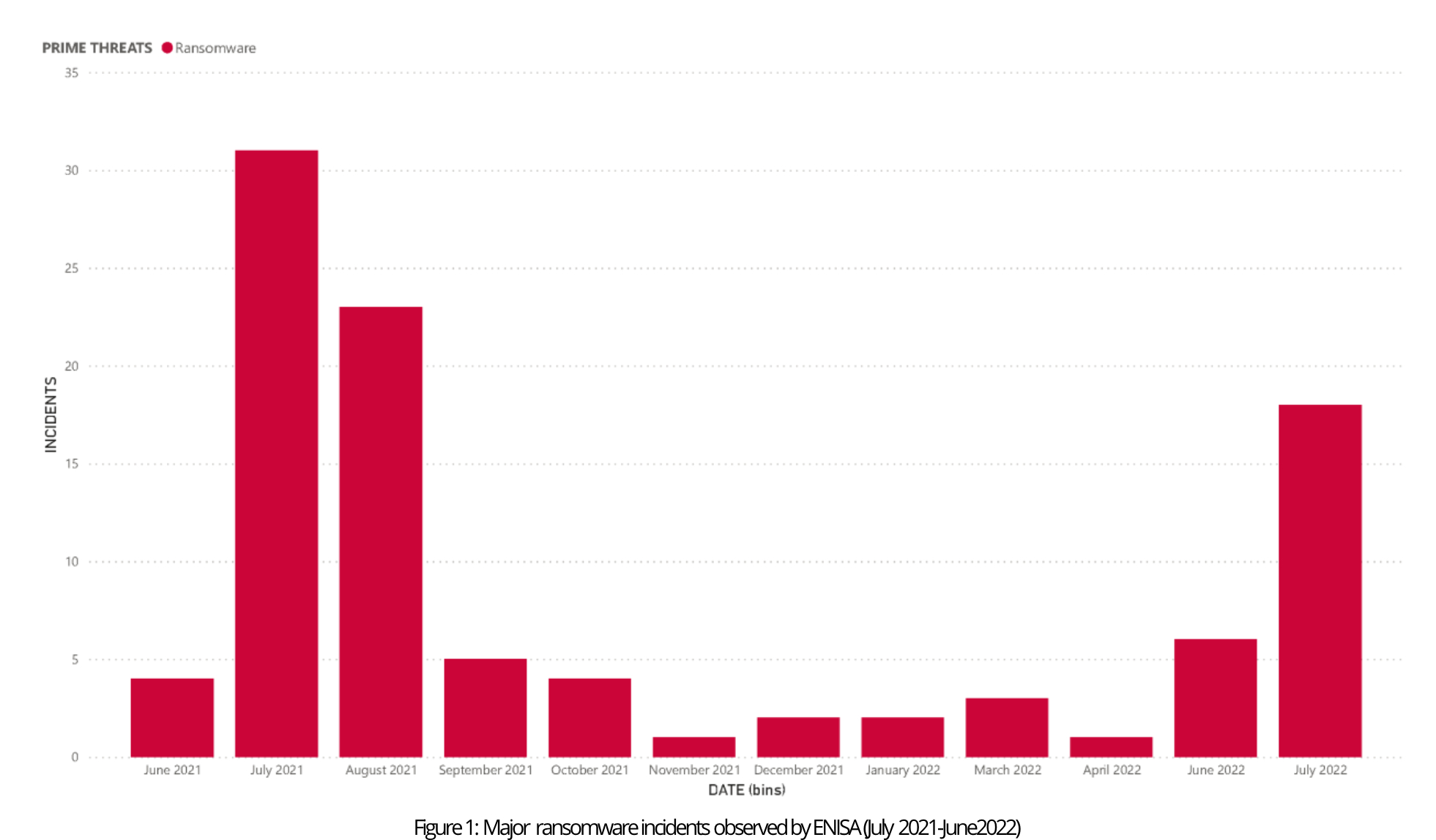
Ransomware trends
1. Ransomware strains
According to research conducted in the first quarter of 2022, LockBit, Conti, and ALPHV (BlackCat) were among the top ransomware strains used in Ransomware as a Service (RaaS) and extortion attacks in terms of victim organisations. Different statistics also confirm LockBit and Conti as the two most active ransomware gangs in Q1 2022, with more than half of all ransomware incidents attributed to them. During Q2 2022, published statistics revealed that LockBit, Conti, and ALPHV accounted for more than half of the victims.
In May 2022, the Conti group took down its attack infrastructure, resulting in its affiliates migrating to other RaaS platforms and groupings like Hive, AvosLocker, and ALPHV.
ALPHV is a newer ransomware strain that emerged at the end of 2021 when the group began recruiting affiliates on hacker forums. This ransomware targets various versions of Linux and Windows 7 and above, and it was developed in RUST.
2. Phishing as the most common initial vector
Like last year’s report, the use of RDP (Remote Desktop Protocol) as an initial attack vector has continued to decrease. However, it remains the second most significant vector for ransomware attacks. Bad actors still exploit RDP vulnerabilities by brute-forcing weak credentials, particularly when MFA (Multi-Factor Authentication) is not enabled. Nowadays, phishing is the most used attack vector to gain an initial foothold in an organization. Both these methods are cost-effective and therefore highly profitable for threat actors
3. Further evolution of extorsion techniques
In traditional ransomware operations, threat actors would gather information before proceeding with further actions, such as extortion, with or without encrypting the files. If the targeted company refuses to pay, the threat actors would make the data public on so-called leak sites, which group all victims of a specific Ransomware-as-a-Service (RaaS) threat actor and are often only available through Tor.
However, starting in June 2022, ALPHV began developing a specialized leak site for individual victims, which was hosted on the public internet. They exposed confidential information pertaining to both customers and employees, including data packs specific to individual employees. Through the website’s functionality, employees or customers could check whether their information was included in the data leak. Disseminating information on the public internet tends to be quicker, gets cached, and indexed, making it an effective way for threat actors to coerce their victims into paying a ransom. Furthermore, it allows third-party victims whose data was leaked to investigate whether they were affected.
4. Leaked information provides a source of priceless information
In February 2022, leaked internal chat logs of the Conti RaaS group provided unique insights into the group’s internal organization, its business operations, and structure. The logs were in Russian and contained documentation, internal software, and other files. The quick start guide provided insights into how the group approached attacks on its victims from a technical perspective, with IoT devices as an essential initial attack surface, and RDP, VPN, and AD as initial backdoors for gaining a persistent presence in the organization’s network. Another interesting piece of information revealed in this leak was that the group worked mainly during the week, and the employees enjoyed benefits such as paid leave.
5. Fast weaponisation of vulnerabilities
The average time to exploit is within eight days of a vendor’s publication of the vulnerability.
This trend highlights the importance of proper patch management and a threat-informed approach to the risk management of vulnerabilities.
6. Payment prohibition
Public entities in North Carolina were banned from paying ransoms, and since June 2022, the state of Florida has also prohibited agencies from paying ransoms and requires them to report any such incidents. The Cyber Incident Reporting Act enforces mandatory reporting of cyberattacks within 72 hours of experiencing an attack and within 24 hours of making a ransomware payment.





0 Comments