Smart Meters in the context of Smart Grid and AMI architecture. Security, Vulnerability and Best Practice – Part 2
The power grid, which is one of the most crucial pieces of critical infrastructure, is on top of the list of interest to various APTs (Advanced Persistent Threat – stealthy threat actor, typically nation or state-sponsored) and other threat actors. Hence the security testing of such solutions as Advanced Metering Infrastructure (AMI) and Smart Meters as well as their security solutions must be of the highest standards.
In this series of articles, SEQRED presents the topic of Smart Meter security in the wider context of the Smart Grid and the AMI architecture.
Last week, we presented the introduction and a synopsis of the AMI architecture. Today’s article covers the analysis of the Smart Meter itself as the possible point of entry to the grid.
Part 2 – Preparing the attack and Smart Meter device security overview
Preparing the attack – vulnerability analysis
In SEQRED’s research project the team’s goal was to put the AMI system through a comprehensive security analysis to identify potential risks and evaluate them from the point of view of a potentially malicious actor. Looking from this point of view one of the key attack entry points (components to compromise first), the most exposed and accessible element of the system, is the Smart Meter itself. These elements are publicly available, often in staircases or electrical boxes outside the property’s fence. Modems and hubs – these components are often not properly secured and, in many cases, accessible from the HAN network – because the end user is often treated as a trusted user in the AMI system’s mobile and web applications.
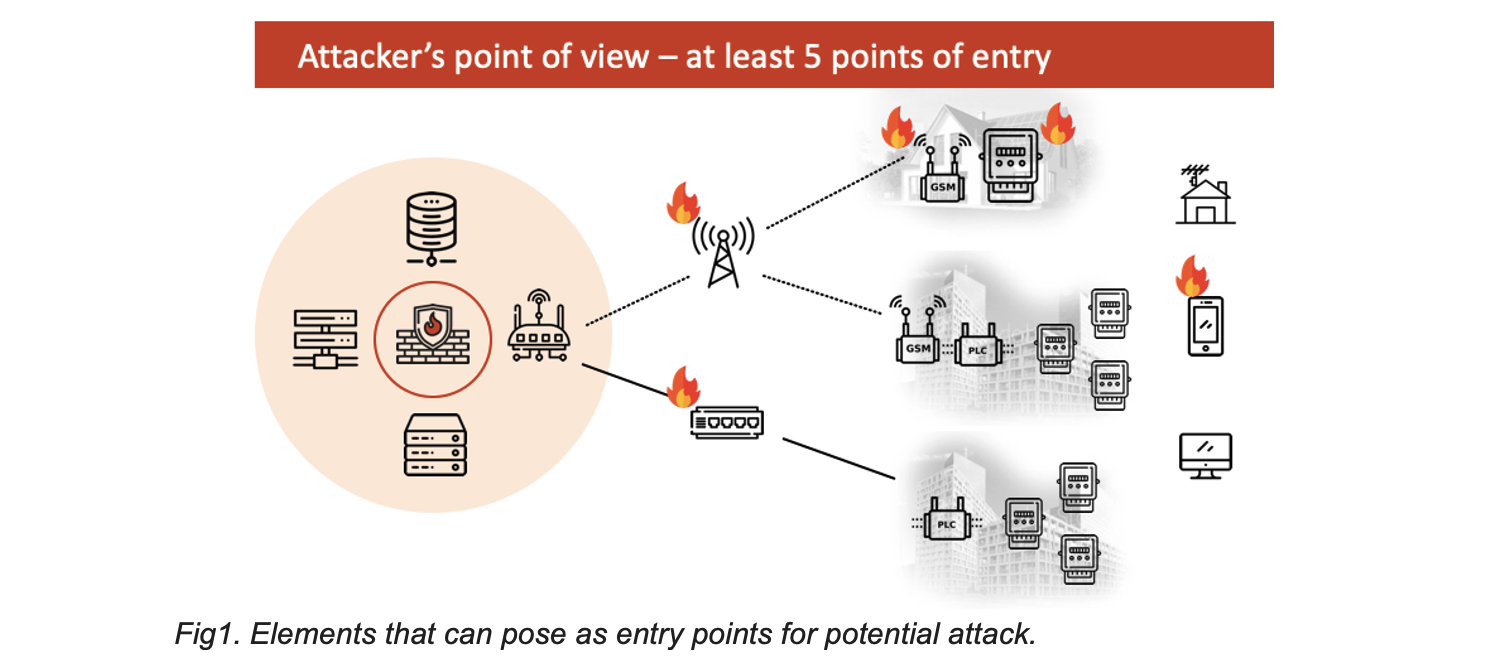
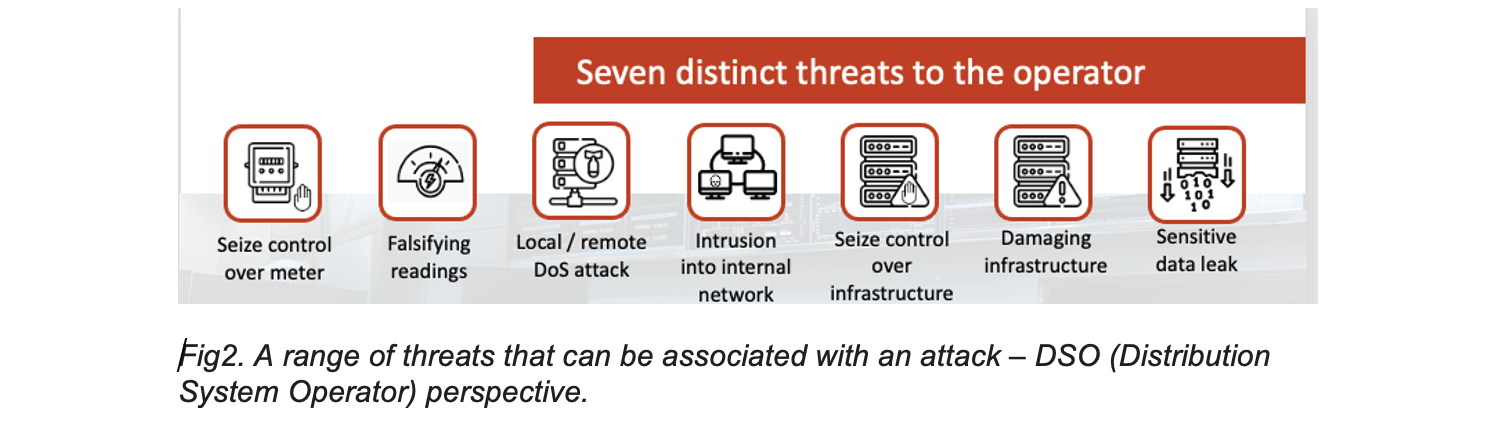
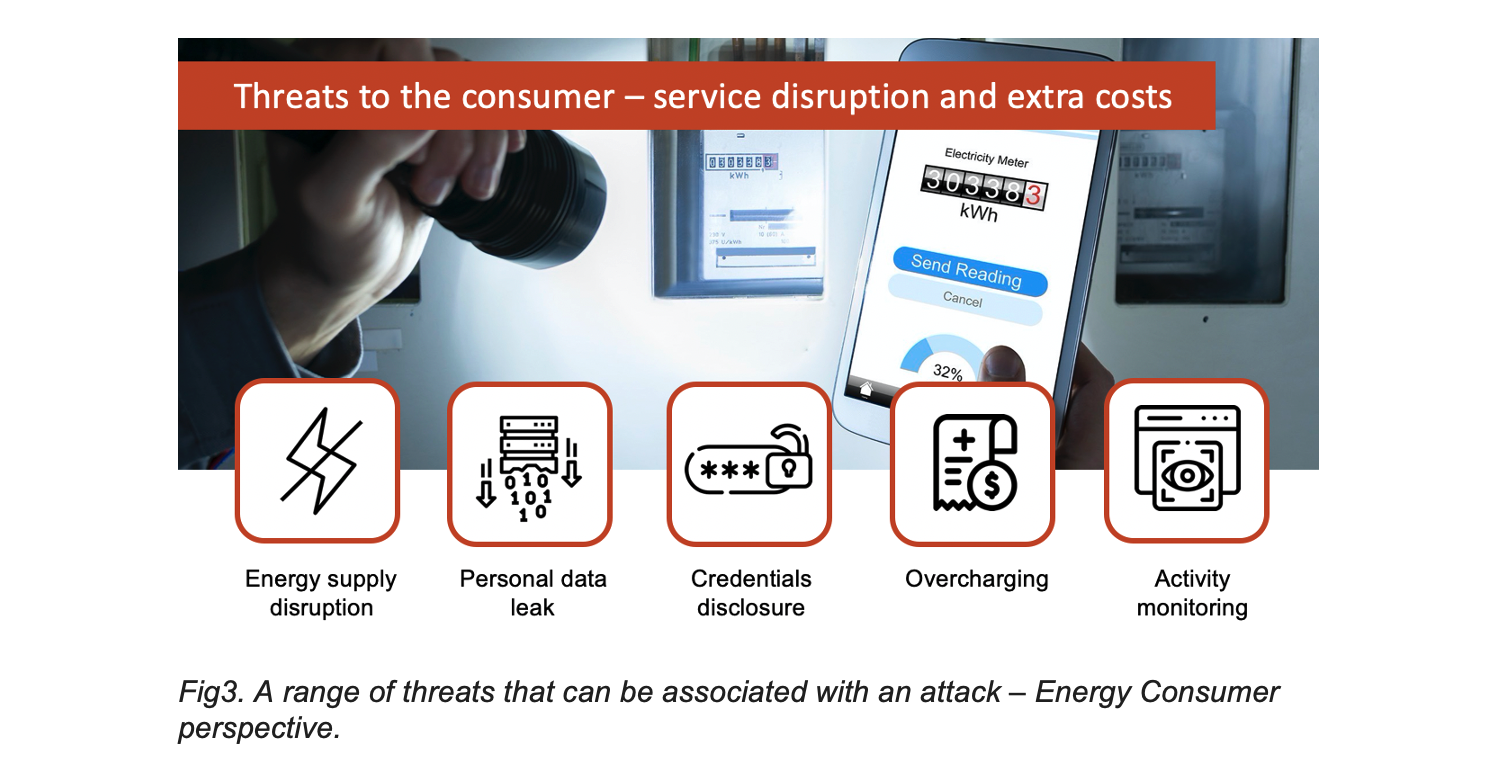
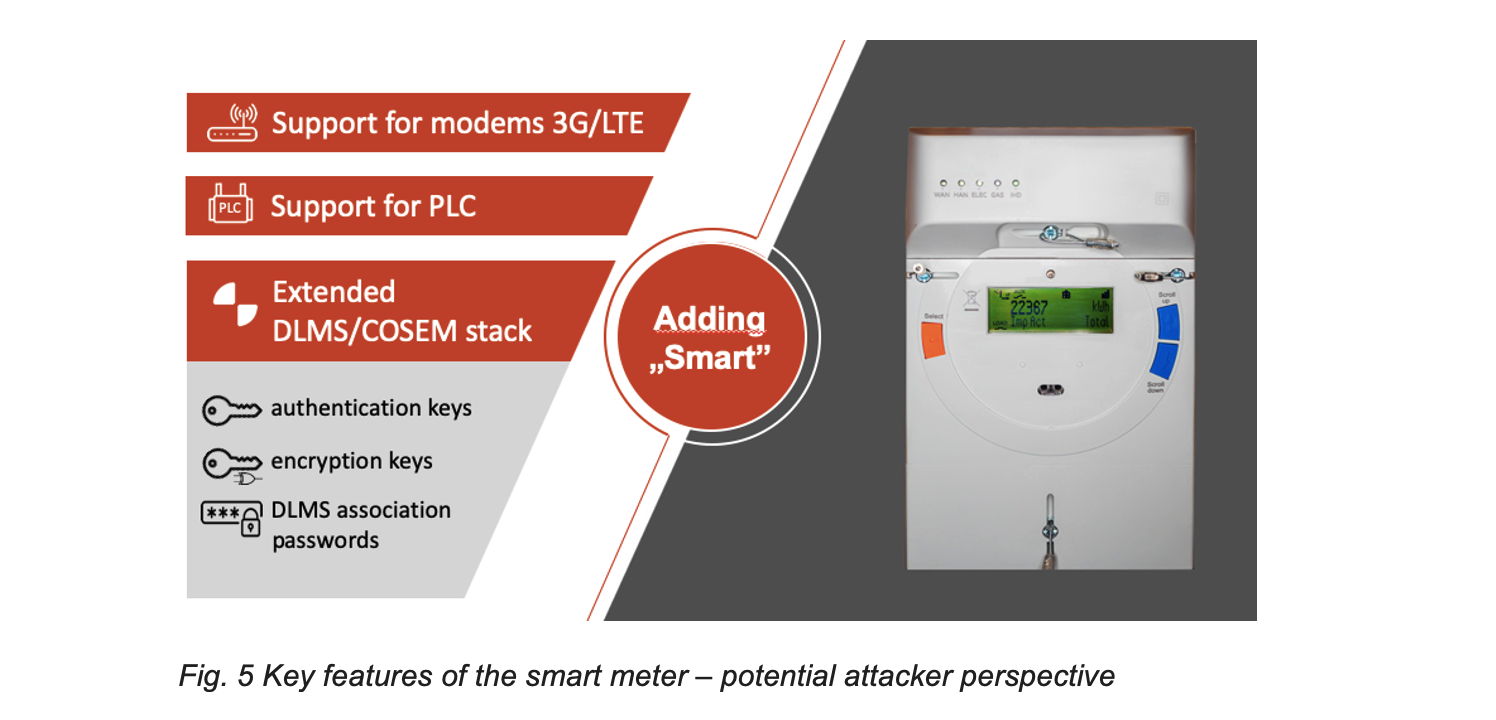
Along with the implementation of AMI systems, new challenges emerged for the meters, which are now smart, mainly relating to the remote communication capability, i.e., support for 3G (or other wireless) modems and the ability to communicate with the use of PLC modules, and above all an extensive DLMS (Device Language Message Specification – IEC 62056) protocol stack implementation. DLMS is the main global standard for smart energy metering, control, and management. It includes specifications for media-specific communication profiles, an object-oriented data model, and an application layer protocol.
As a result, new obligations were placed on the energy distributors because such meters, as well as modems, should be managed and maintained, and it should be able to communicate with them according to the standard, keep passwords and keys for DLMS associations, update software, and above all provide infrastructure for the meters to have the means to communicate.
Smart Meter device security overview
Components of a smart meter
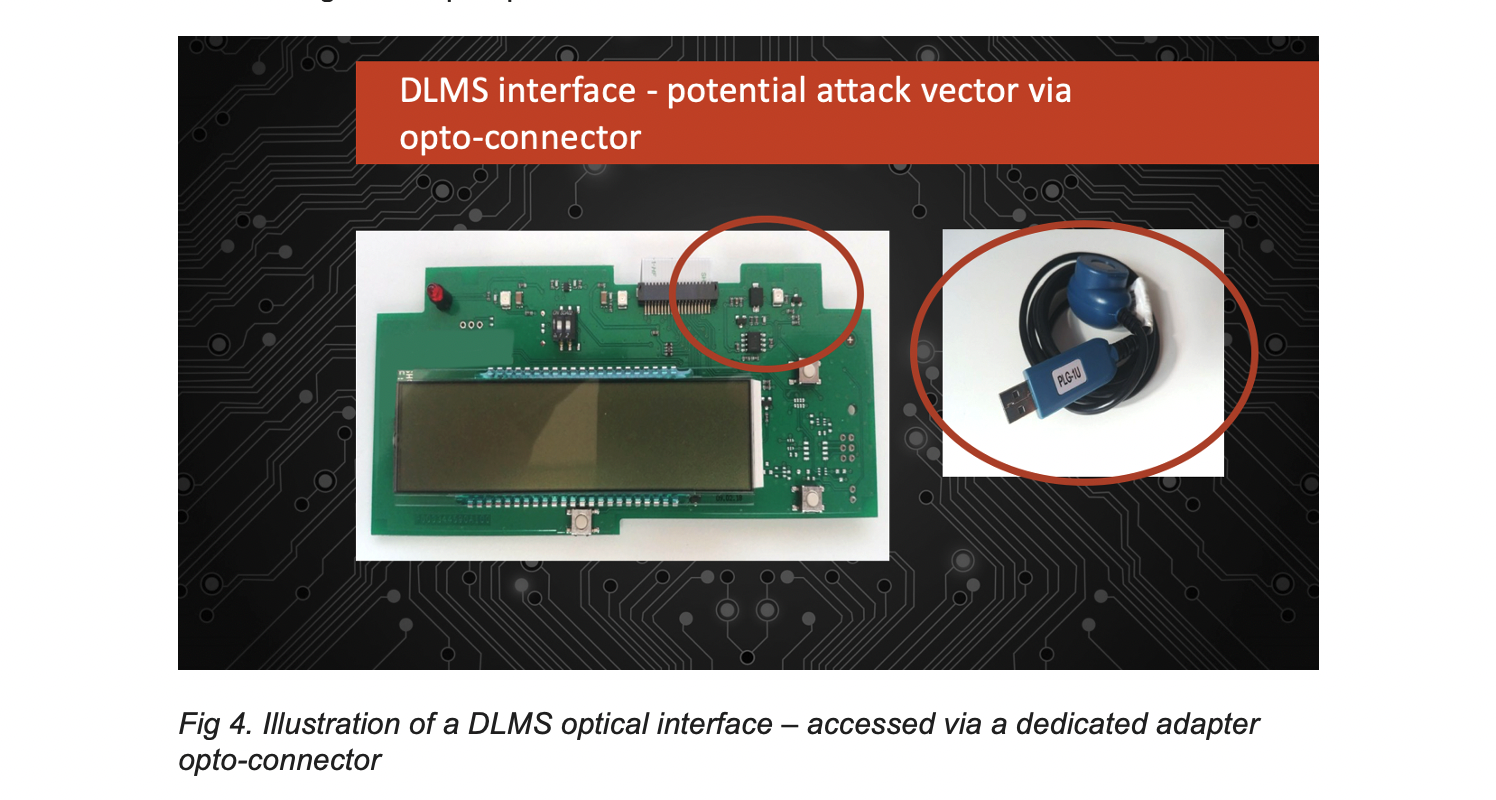
The heart of the meter contains a microcontroller (most often in arm or mips architecture), analog-to-digital converters, a display, communication modules mentioned earlier, as well as the most important element – an opto-connector, which is a public element of the meter anyone can approach and use it to connect with the meter using the adapter presented below.
It is important to mention that from the security point of view any device, including a smart meter can be subject to a reverse engineering process which allows to map out its internal structure and the logic of the built-in program (firmware).
The interface of the most interest was the one mostly available – the opto-connector as it is widely used for communication. The adapter can be attached to a laptop or smartphone. The opto-connector is used for communication with the meter where the standard communication is carried out using the DLMS/COSEM protocol. The DLMS/COSEM standard describes the method of communication with smart meters regardless of the transport layer used (e.g., TCP / IP, opto-connector). It also defines a protocol that conforms to the OSI model and models of interfaces and objects transmitted in messages that conform to that protocol. Like any such protocol, its implementations may be susceptible to programming errors that can be used (exploited) with the help of messages prepared by the attacker.SEQRED’s team decided to check the security of one of the most popular DLMS/COSEM implementations. The choice fell on the solution used for 20 years in countries across Europe and OEMed by many smart meters manufacturers. What’s important for the research efficiency was open-source development and implementers provided an example program simulating the operation of the meter. Tests were conducted using the intelligent fuzzing method, i.e., by introducing random input data into the program and using a genetic algorithm that makes the new input data more like that discovered by new paths in the program’s code. The screenshot below shows the fuzzer execution result – identifying 15 unique crashes, i.e., input data that caused the program to stop abnormally in a different way. Further analysis revealed that the crushes resulted from 5 programming errors identified (and reported to implementers) by SEQRED. Errors of this type allow denial of service attacks, reading data in the meters’ RAM memory (including passwords, for example), or code execution, i.e., in practice the attacker can take control of the meter. It should be added that even if access to the meter required a password, errors occurred before it was verified – e.g., as in the case of the error presented in the screenshot below when agreeing on the version of the protocol used in further communication. This means that the attacker could have used it without knowing such a password.
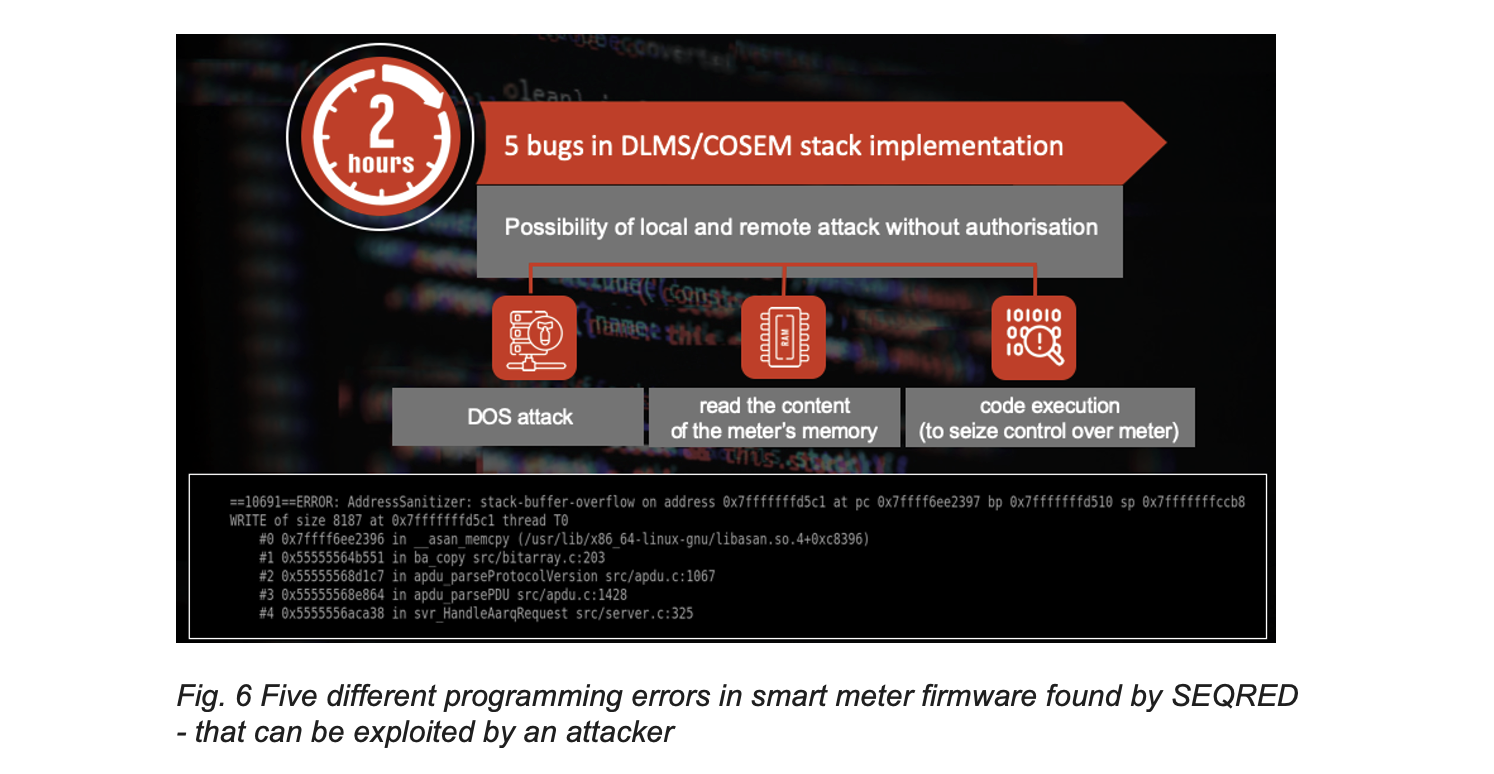 An interesting fact: the shortest input frame causing the meter to stop working was only 22 bytes long. At this point SEQRED had several vulnerabilities identified, and DLMS frames allowed to disrupt and take over the meter. The decision was made to try to reproduce errors in physical smart meter devices commonly used in the European market.
An interesting fact: the shortest input frame causing the meter to stop working was only 22 bytes long. At this point SEQRED had several vulnerabilities identified, and DLMS frames allowed to disrupt and take over the meter. The decision was made to try to reproduce errors in physical smart meter devices commonly used in the European market.
Next week, we will present the results of a controlled attack on a Smart Meter.





0 Comments