Defense-in-Depth Architecture Capabilities

A growing number of organizations are adopting digital transformation initiatives that involve modifying their operational technology (OT) environments and formulating plans to establish a multi-tiered information architecture that aligns with their business objectives. These goals may include the following:
- Ensuring the proper upkeep of field devices, telemetry collection, or industrial-level process systems
- Improving data collection and dissemination capabilities
- Enabling remote access to critical systems and information.
In response to evolving local and global demands and regulations, organizations are progressively integrating their information technology (IT) and operational technology (OT) systems. To enhance their cybersecurity posture, they can adopt a defense-in-depth approach that employs a layered security framework encompassing people, processes, and technology. This strategy can reinforce their overall defense against cyber threats and make it harder for malicious actors to infiltrate their environment undetected. The subsequent sections will examine individual defense-in-depth layers and provide organizations with practical suggestions and recommendations to create and implement their defense-in-depth cybersecurity architecture.
The layers are:
Layer 1– Security Management
Layer 2 – Physical Security
Layer 3 – Network Security
Layer 4 – Hardware Security
Layer 5 – Software Security
Layer 1 – Security Management
The security management or governance function serves as the fundamental cybersecurity program for the OT environment. The programmatic and organizational decisions made at this level will significantly influence the decisions regarding the other defense-in-depth layers. Consequently, organizations should prioritize completing this layer before embarking on the implementation of the other layers.
Layer 2 – Physical Security
Physical security measures aim to mitigate the possibility of unintended or deliberate loss or harm to assets and the surrounding environment. These assets may comprise control systems, equipment, tools, the immediate surroundings, the community, and sensitive intellectual property, such as process configurations and customer information. When deploying physical security measures to safeguard their environments, organizations must also address supplementary considerations, such as environmental, safety, regulatory, and legal requirements.
To create a robust defense-in-depth physical security solution, organizations should consider the following attributes:
To safeguard physical locations, organizations often employ a layered security approach that creates several physical barriers around buildings, facilities, rooms, equipment, or other critical assets. Physical security controls may include fences, anti-vehicle ditches, earthen mounds, walls, reinforced barricades, gates, door and cabinet locks, guards, or other measures.
Effective physical access control involves locking equipment cabinets when not in use and ensuring that wiring is organized and within cabinets or under floors. Additionally, all computing and networking equipment should be kept in secured areas. The keys of OT assets such as PLCs and safety systems should be kept in the “Run” position at all times unless they are being actively programmed.
Access monitoring systems such as still and video cameras, sensors, and identification systems like badge readers, biometric scanners, and electronic keypads can help monitor and record the physical presence or absence of individuals, vehicles, animals, or other entities. Such systems typically do not prevent access but can provide evidence and alert upon detection of unauthorized access. Adequate lighting should be provided based on the type of access monitoring device deployed.
To enhance safety and security, organizations can use people and asset tracking technologies to locate people and vehicles within their facilities. This enables them to ensure that personnel and vehicles remain in authorized areas, identify individuals requiring assistance, and support emergency response efforts.
Layer 3 – Network Security
Building on physical security, organizations need to examine network communications and protect the devices and data used to support their OT environment. Although network security encompasses many facets, this section focuses on fundamental components that can aid organizations in planning and implementing their network security capabilities. These include applying network architecture principles of segmentation and isolation, centralizing logging, network monitoring, and protection against malicious code. Additionally, this section will address zero-trust architecture (ZTA) and considerations for implementing these architectural improvements in an OT environment.
Network Architecture
A recommended practice for network architectures is to segment and isolate IT and OT devices. Organizations can initiate this process by determining how to categorize devices. For example, devices can be segmented based on management authority, level of trust, functional criticality, data flow, location, or other logical combinations. Organizations may also opt to use a recognized industry model, such as the Purdue Model [Williams], ISA-95 Levels [IEC62264], Three-Tier IIoT System Architecture [IIRA19], or a blend of these models, to arrange their OT network segmentation. Another option for network segmentation that organizations can consider is incorporating the concept of a Demilitarized Zone (DMZ) as an enforcement boundary between network segments. Implementing network segmentation through levels, tiers, or zones allows organizations to regulate access to sensitive information and components while also taking into account operational performance and safety.
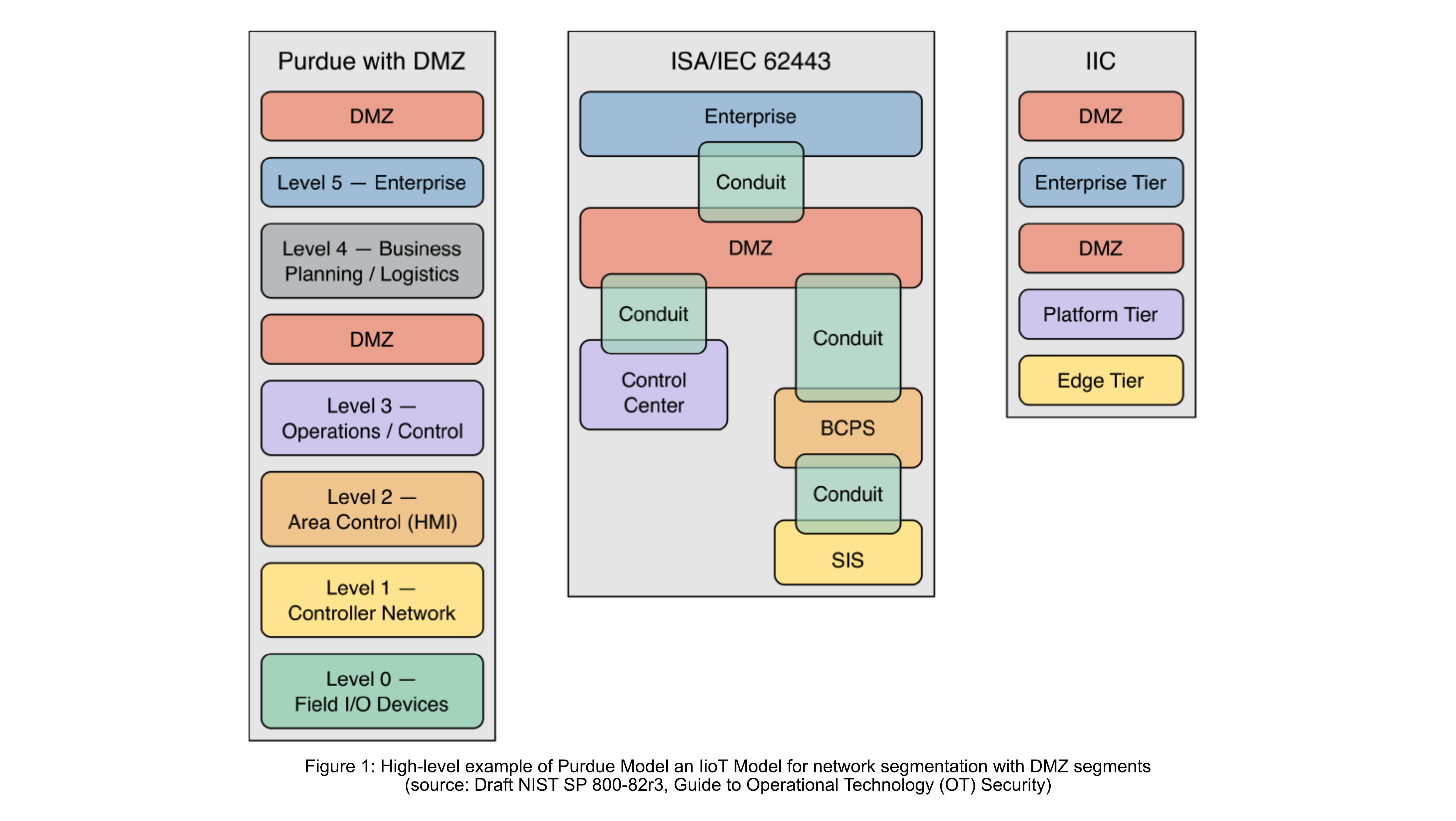
When network architectures are configured appropriately, they can support segmentation and isolation by enforcing security policies and controlling network communications. To identify the necessary communications, organizations usually refer to their mapped data flows. These requirements are then integrated into the network architecture and configured in the policy engines of network devices to enable monitoring of communication between segments and allow only authorized communications. Network devices that support traffic enforcement capabilities such as switches, routers, firewalls, and unidirectional gateways/data-diodes can be used to implement network segmentation and isolation.
Firewall
Firewalls are commonly utilized as boundary protection devices to control the flow of information and connections between network segments, supporting network isolation. They can be deployed as standalone devices or directly on hosts. Firewall rulesets must be established to only allow connections between adjacent levels, tiers, or zones. For instance, if an organization is using a Purdue model architecture, firewall rules and connection paths should be implemented to prevent Level 4 devices from communicating directly with Level 2, 1, or 0 devices. Similarly, ISA/IEC 62443 or Industrial IoT Consortium (IIC) architectures would follow a similar concept.
One aspect that varies in firewall rules is the control of outbound traffic from the control network. Allowing outbound connections from lower levels, tiers, or zones can pose a considerable risk if unmanaged. Outbound rules must be just as stringent as inbound rules to minimize these risks.
Alternatively, organizations can use a unidirectional gateway or data diode that permits authorized communication in only one direction. Using unidirectional gateways can offer additional protection against system compromises at higher levels or tiers within the environment. For instance, a unidirectional gateway placed between Layers 2 and 3 can safeguard Layer 0, 1, and 2 devices from a cybersecurity incident that occurs at Layers 3, 4, or 5.
Centralized Logging
To support monitoring, alerting, and incident response analysis, it is essential to configure network devices such as routers, gateways, switches, firewalls, servers, and workstations to log events. Applications, operating systems, and network communications typically have logging capabilities. To effectively manage these logs, organizations should consider implementing a centralized log management platform that supports log retention, monitoring, and analysis efforts. Such a platform can assist with identifying and investigating suspicious activity and detecting potential security breaches. By monitoring log data, organizations can identify patterns of behaviour that indicate potential threats and take appropriate action to mitigate them.
Network Monitoring
Network monitoring is the practice of analysing alerts and logs to detect potential cybersecurity incidents. To support this effort, organizations can use tools like Behaviour Anomaly Detection (BAD), Security Information and Event Management (SIEM), and Intrusion Detection/Prevention Systems (IDS/IPS) to monitor network traffic and receive alerts for unusual or suspicious activity. In addition, organizations should consider other capabilities such as asset management to discover and inventory network devices, baseline typical network traffic and data flows, diagnose performance issues, and identify misconfigurations or malfunctions of networked devices. To enhance their network monitoring capabilities, organizations may also consider incorporating services such as threat intelligence monitoring.
Zero-Trust Architecture (ZTA)
Zero Trust Architecture (ZTA) is a cybersecurity approach that emphasizes protecting resources, such as data and information services, by continuously evaluating authorization decisions made closer to the resource being requested, rather than implicitly granting broad access to users once inside the network perimeter. Traditional network security relies on perimeter defenses and segmentation, which may not mitigate lateral movement risks within a zone. With the emergence of distributed computing, wireless and cellular communications, and cloud and hybrid-cloud environments, traditional network perimeters are becoming less defined, making ZTA an attractive option for organizations. However, implementing ZTA comes with some challenges, including the need to integrate several technologies with varying maturity levels to support the environment, as there may not be a single solution available. Additionally, migrating to a ZTA may require more investments in time, resources, and technical expertise.
Layer 4 – Hardware Security
Hardware security mechanisms serve as the basis for ensuring security and trust in devices deployed within an environment. After device trust is established, it is essential to maintain and monitor the device state in accordance with the system model and security policy. To enable these functions, vendors often offer embedded technologies, such as the Trusted Platform Module (TPM), or hardware implementations of advanced encryption standards (AES) and secure hash algorithms (SHA). These hardware security features can enhance endpoint devices to meet specific security requirements, including:
- Monitoring and analysis
- Secure configuration and management
- Endpoint hardening
- Integrity protection
- Access control
- Device identity
- Root of trust
- Physical security
Layer 5 – Software Security
Software security protection mechanisms offer organizations the ability to ensure that the applications and services used to support OT are being used and maintained securely. The use of software security mechanisms can improve endpoint security by implementing:
- Application whitelisting
- Patching
- Secure code development
- Configuration management, including application hardening
Application whitelisting
Allowlisting technologies for applications provide an additional layer of protection on hosts by limiting the execution of applications to only those that are authorized. When appropriately configured, unauthorized applications will not be able to run on the host environment.
Patching
The primary goal of patching is to fix vulnerabilities in software, although it may also enhance functionality. Patch management is a vital defense-in-depth capability that supports organizational risk management. However, deploying patches in operational technology (OT) environments requires additional considerations, such as testing and validation to ensure they do not affect operations or safety. OT systems may require continuous operation or have limited maintenance windows, making it difficult to apply patches. In some cases, updating the OS or implementing additional controls may be necessary to protect the environment from known vulnerabilities. Organizations can configure tools like web application firewalls (WAF) and intrusion prevention systems (IPS) to provide additional protection while waiting for patches. Prioritizing patching in DMZ environments and for vulnerabilities that could impact availability, integrity, or allow unauthorized access is crucial. Patches should be tested on a sandbox system and deployed during scheduled maintenance windows, with a recovery plan in place in case of issues. Different levels or zones may have varying availability requirements, and organizations should plan patching accordingly.
Secure Code Development
Organizations that develop their own systems and components should include policies and procedures to support and validate secure code development practices as part of their cybersecurity program. Security should be integrated into each phase of the software development life cycle (SDLC), including security reviews and coding techniques for the following processes:
- Utilizing or developing tools to automate secure code techniques and perform audits
- Testing and reviewing code to ensure compliance with secure coding practices
- Conducting security testing on the software to identify programming errors For organizations that obtain components or services from third parties, it is important to review these same practices before entering into contracts with vendors. Organizations can encourage the industry to adopt more secure products by including these practices in their service-level agreements and procurement actions.
Configuration Management
Incorporating configuration management practices for cybersecurity settings is crucial to meet organizational and regulatory security requirements. Secure configurations and application hardening settings are implemented to restrict access and protect data at rest or in transit. Application hardening may involve disabling network communication ports, application features, or unnecessary services running on the system. Encryption is also an effective defense mechanism in OT security, where data is encrypted while in transit or at rest to prevent unauthorized viewing or modification. However, encryption adds latency and may not be feasible for all OT devices. Organizations should weigh the benefits and drawbacks of encryption and make informed decisions about where to include encryption in their defense-in-depth strategy.





0 Comments