ENISA’s Threat Landscape Report 2022 – Part 2 – Prime Threats by Proximity and Sector

Prime Threats by Proximity to the EU
In the context of the ENISA Threat Landscape, it is crucial to take into account the proximity of cyber threats to the European Union (EU). This is essential for assisting analysts in evaluating the severity of cyber threats, linking them to potential threat actors and attack methods, and determining appropriate mitigation strategies.
ENISA classifies cyber threats into four categories as follows:

Using this classification to describe the proximity and strength of the impact of a prime threat ENISA has comprised graphics, depicting the occurrence of the prime threats between July 2021 and July 2022.
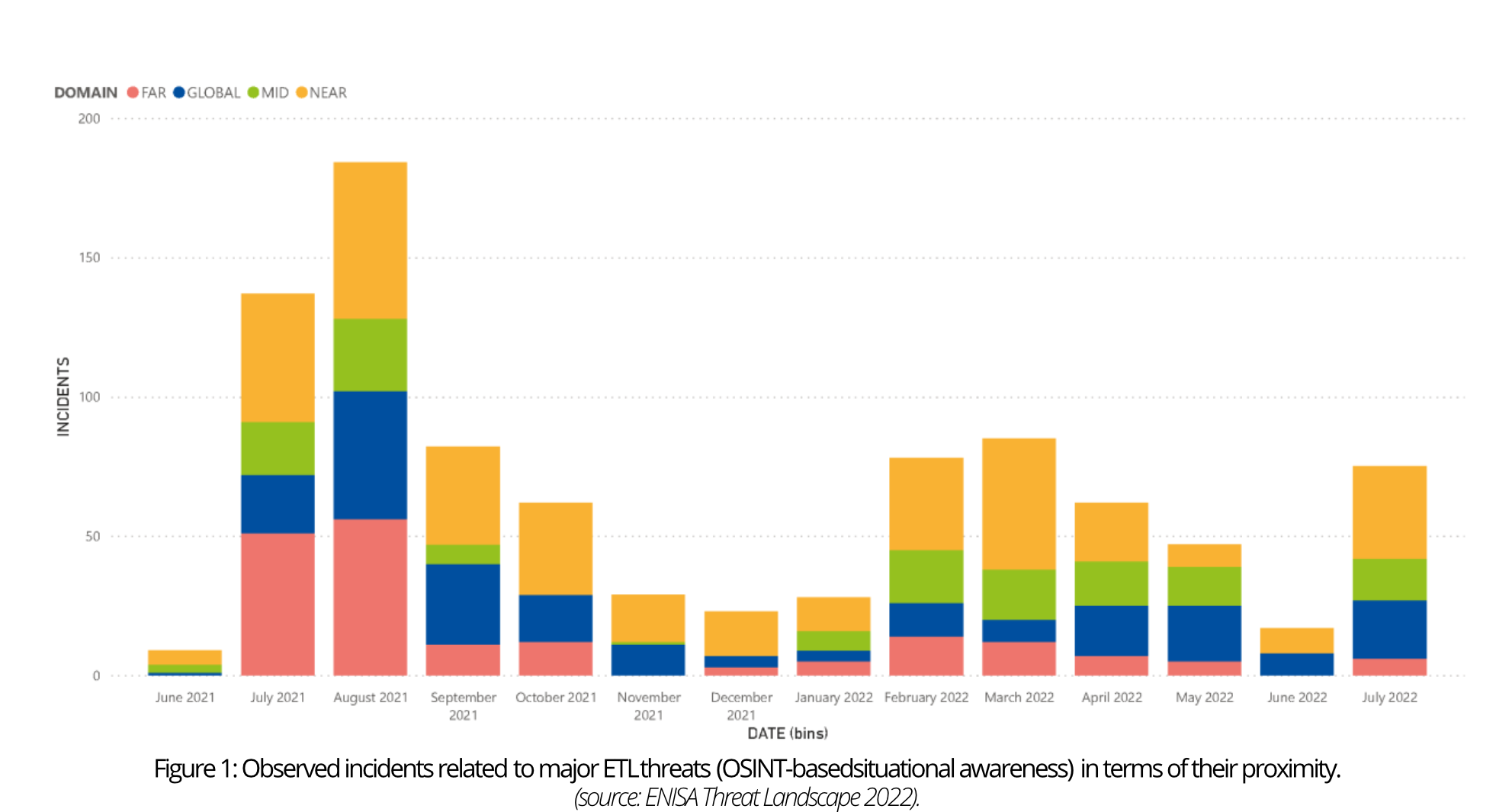
As shown in the figure above, the number of incidents in 2022 has decreased compared to 2021. This may be attributed to the ongoing incident handling and analysis, which affects reporting. Additionally, the open-source nature of information collection in the ETL could introduce unintentional bias in the results. Notably, the NEAR category consistently reports a high number of incidents related to significant threats, underscoring their importance in the EU context.
Prime Threats by Sector
Cyber threats do not typically affect a single sector exclusively, but rather have the potential to impact multiple sectors. This is often the case when vulnerabilities in underlying ICT systems are exploited across various industries. However, targeted attacks and those that take advantage of differences in cybersecurity maturity or sector popularity should also be taken into consideration when prioritising mitigating actions. These factors can lead to incidents occurring more frequently in certain sectors, highlighting the need to thoroughly investigate sector-specific aspects of observed threats and incidents.
The following graphics show the number of incidents related to prime threats of ETL 2022 per sector.
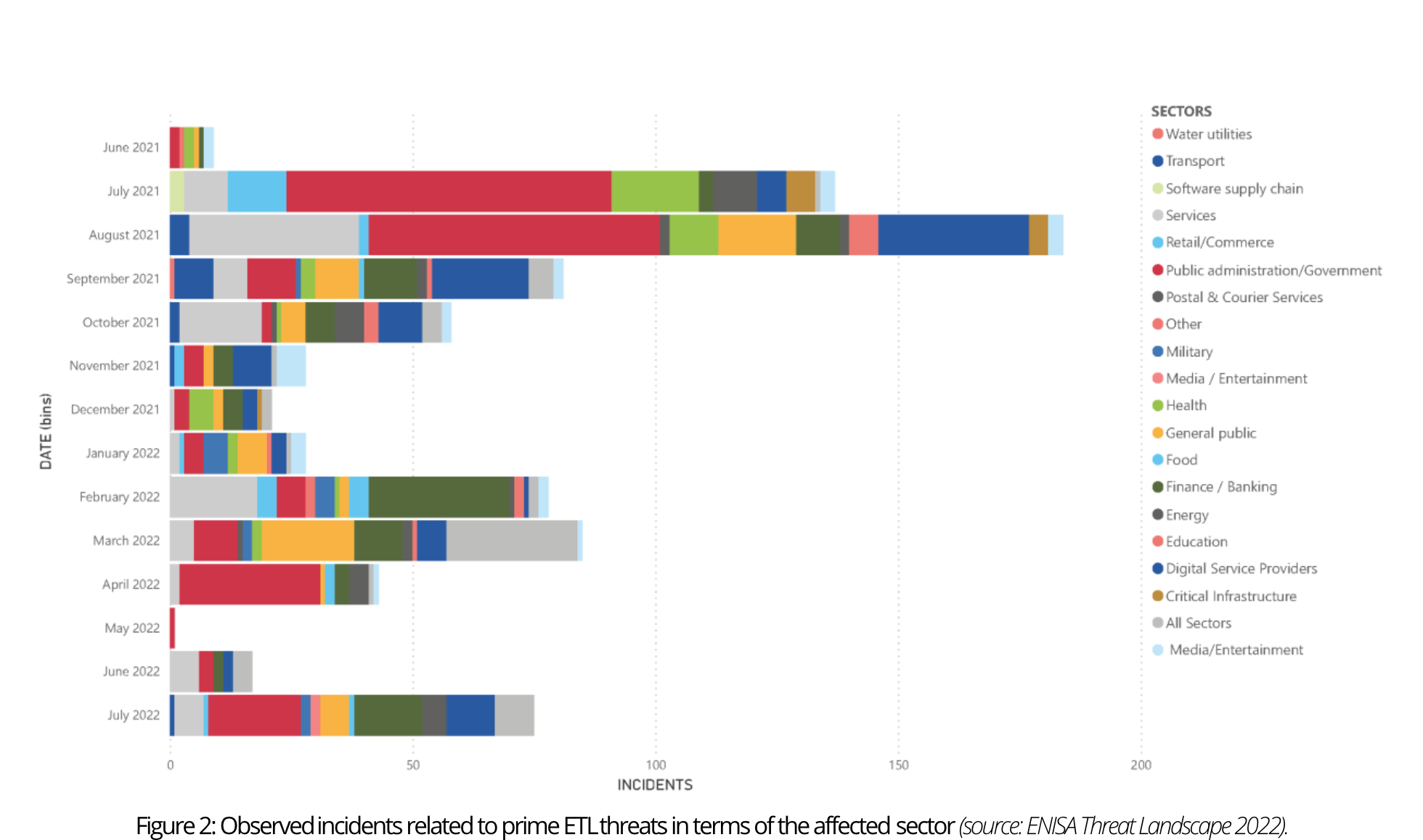
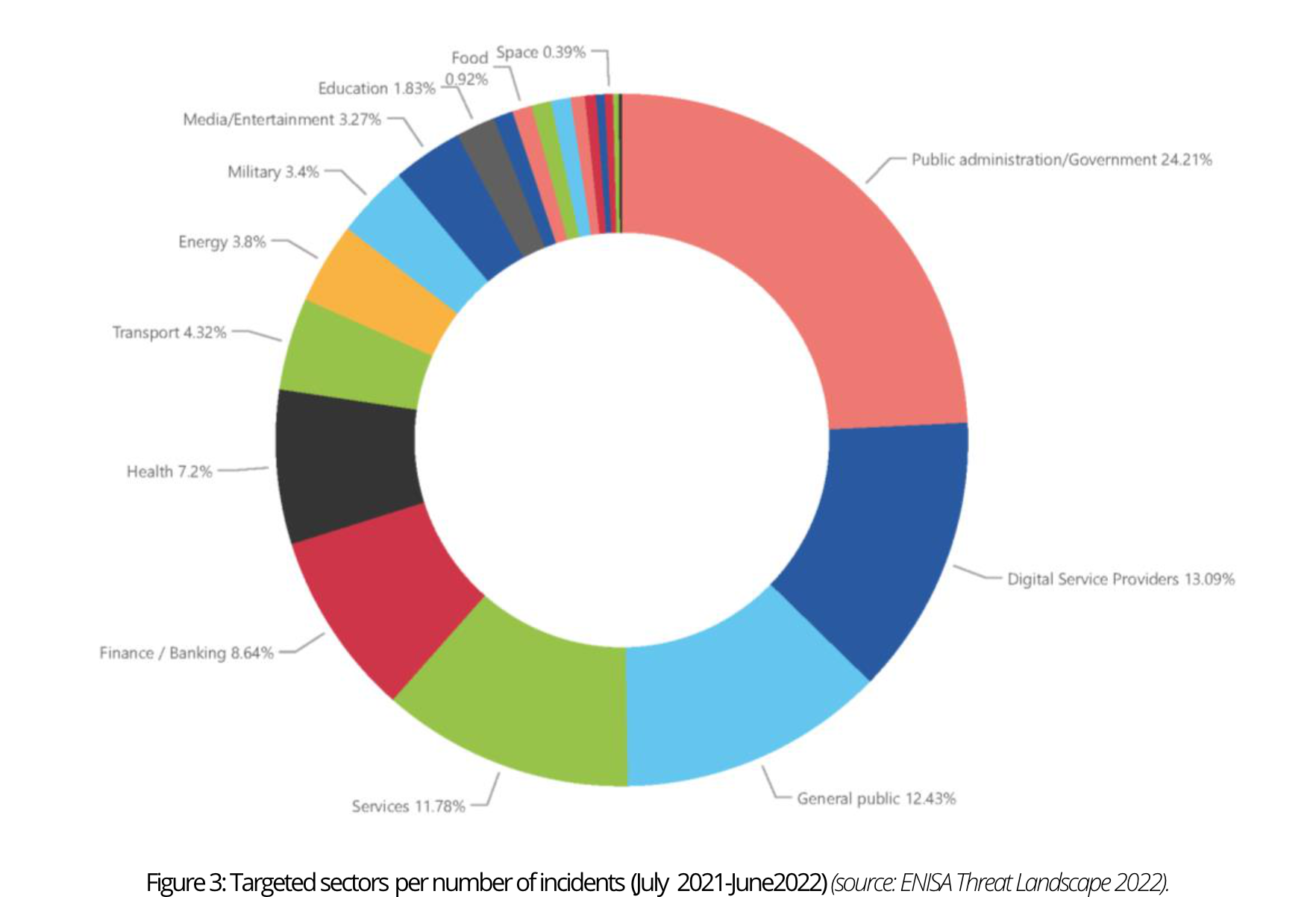
The graphics show a substantial number of incidents directed toward public administration, government, and digital service providers. This shouldn’t come as a surprise given the extensive cross-sector impact of horizontal service provision in this industry. Moreover, a noteworthy number of incidents targeted the general public rather than specific sectors. Notably, the finance sector experienced a consistently high number of incidents throughout the reporting period, with the health sector closely following.
Impact Assessment by Sector
In this edition of ENISA’s threat landscape, an impact assessment of the observed incidents during the reporting period has been included. Through a qualitative impact analysis process, ENISA aims to identify the potential consequences of a disruptive cyber incident by categorizing five types of potential impacts and assigning corresponding levels of severity – high, medium, low, or unknown. However, since information regarding the impact of a cybersecurity attack is often undisclosed for security reasons, assessing the effect following an incident involves assumptions, which may introduce a level of subjectivity.
ENISA distinguishes the following types of impact:
- Reputational impact refers to the potential for negative publicity or an adverse public perception of the entity that has been the victim of a cyber incident.
- Digital impact refers to damaged or unavailable systems, corrupted data files or exfiltration of data.
- Economic impact refers to the direct financial loss incurred, the damage to national security that can be caused due to the loss of important material, or a ransom requested.
- Physical impact refers to any kind of injury or harm to employees, customers, or patients.
- Social impact refers to any effect on the general public or to a widespread disruption that could have an impact on society (e.g., incidents disrupting the national health system of a country).
The Reputation of the Public Administration sector suffered the most, followed by the Finance sector, most likely because of loss of trust in the targeted entity.
In most sectors, the Digital impact of incidents was classified as medium to low, except for Public Administration, Finance, and Digital Service Providers. These sectors experienced incidents with high impacts, usually due to ransomware attacks.
Regarding Economic losses, the Public Administration and Finance sectors experienced some of the most substantial impacts. This can be attributed to numerous breaches that involved stealing banking information or personal details, in addition to the public sector being the primary focus of ransomware attacks that year.
The Physical impact continues to be the least understood impact due to the absence of published information or credible data.
The Public Administration sector experienced the most incidents related to Social impact, which typically involved service disruptions or personal data breaches. Moreover, the Health sector also saw a significant number of incidents classified as ‘high’ impact due to either sensitive data breaches or health services being disrupted, such as appointment bookings becoming unavailable.
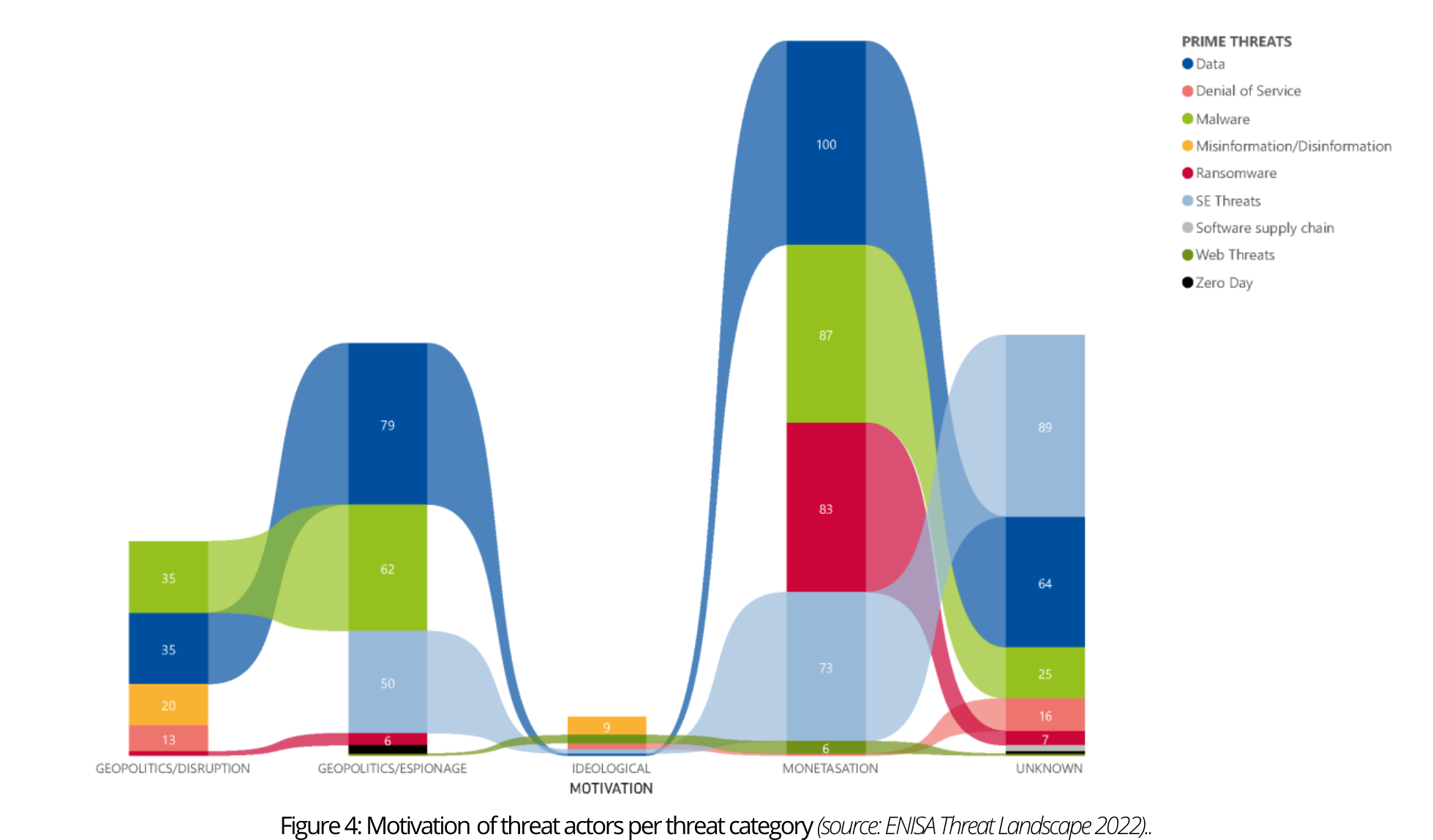
Prime Threats by Motivation
Comprehending the adversary and the rationale behind a cybersecurity incident or targeted attack is crucial as it can reveal what the attacker is seeking. Understanding the motives aids organisations in deciding what to safeguard and how to safeguard it, as well as providing insight into the attacker’s intentions and enabling entities to concentrate their defense efforts on the most probable attack scenario for a given asset.
For this purpose, four different kinds of motivation have been defined that can be linked to threat actors:
- Monetisation: any financially related action (carried out by cybercrime groups);
- Geopolitics/Espionage: gaining information on IP (Intellectual Property), sensitive data, and classified data (mostly executed by state sponsored groups);
- Geopolitics/Disruption: any disruptive action done in the name of geopolitics (mostly carried out by state-sponsored groups);
- Ideological: any action backed up with an ideology behind it (such as hactivism).





0 Comments