Threat Sources, Vulnerabilities, and Incidents – part 3

System Vulnerabilities and Predisposing Conditions
The weaknesses present in a system can originate from its hardware, firmware, and software elements. These vulnerabilities can result from various factors such as design deficiencies, development errors, misconfigurations, insufficient maintenance, ineffective administration, or interactions with other systems and networks.
In summary, the typical vulnerabilities and underlying factors often observed in OT systems can be classified into the following categories:
1. Architecture and Design Vulnerabilities and Predisposing Conditions
2. Configuration and Maintenance Vulnerabilities and Predisposing Conditions
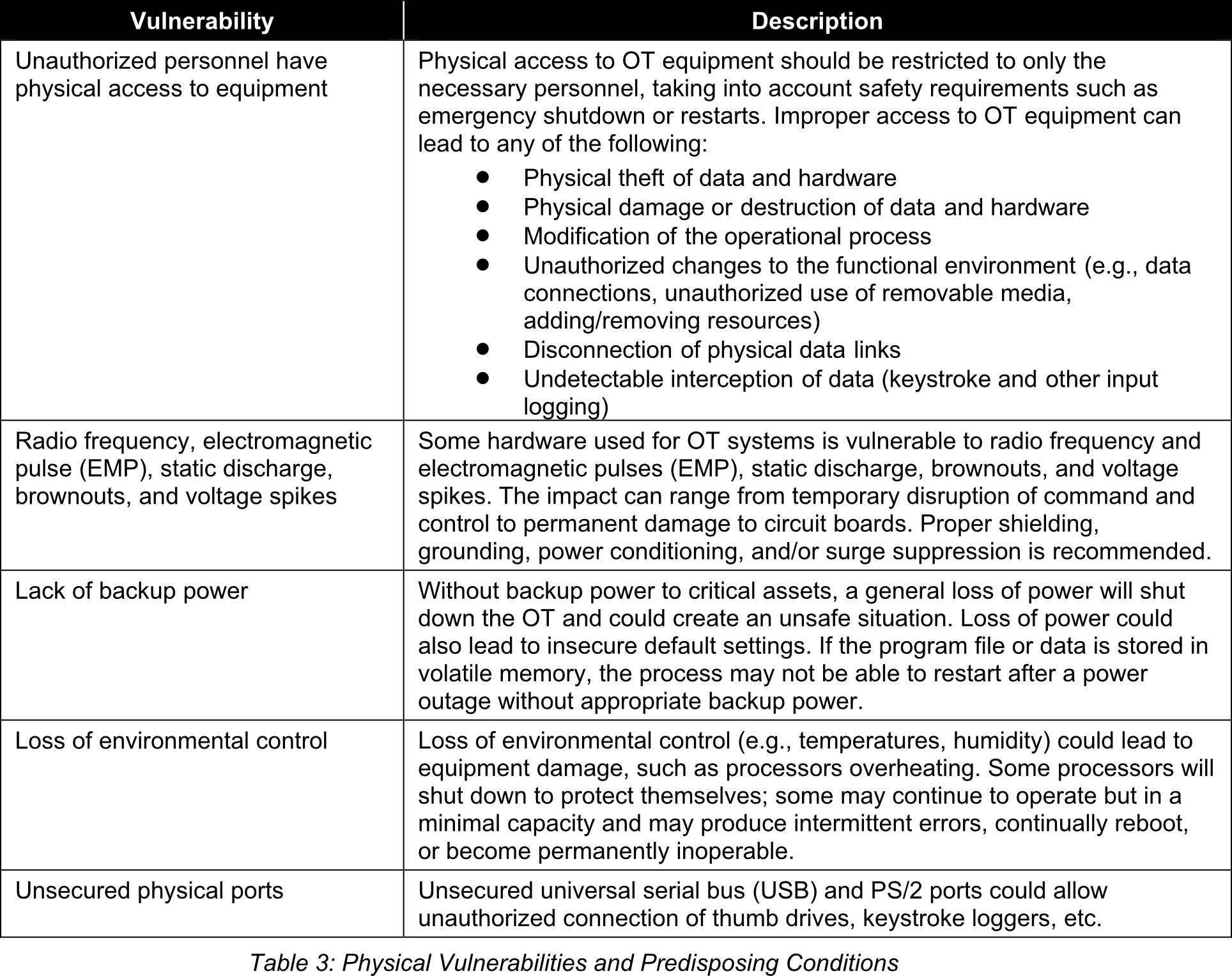
3. Physical Vulnerabilities and Predisposing Conditions
4. Software Development Vulnerabilities and Predisposing Conditions
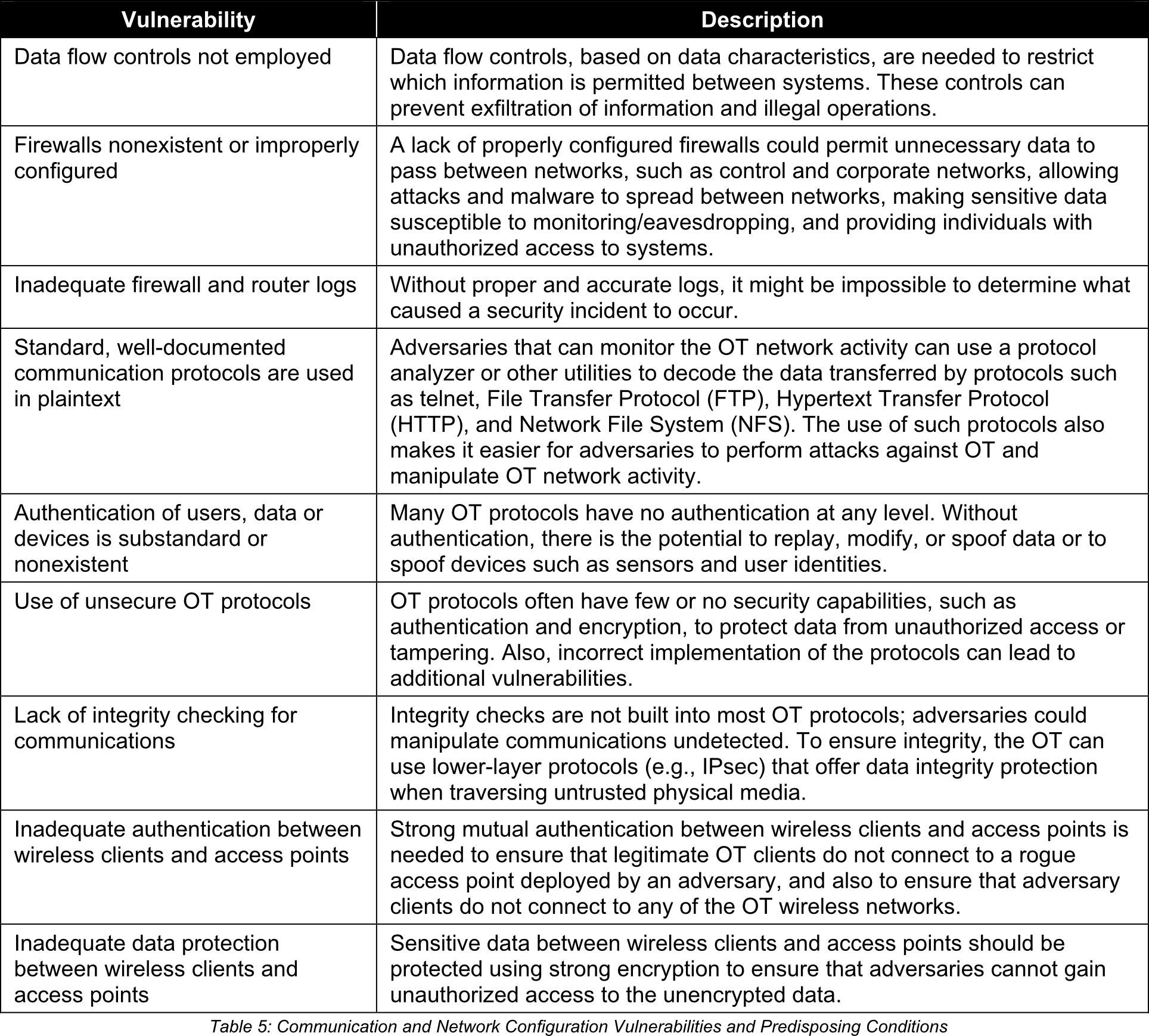
5. Communication and Network Configuration Vulnerabilities and Predisposing Conditions
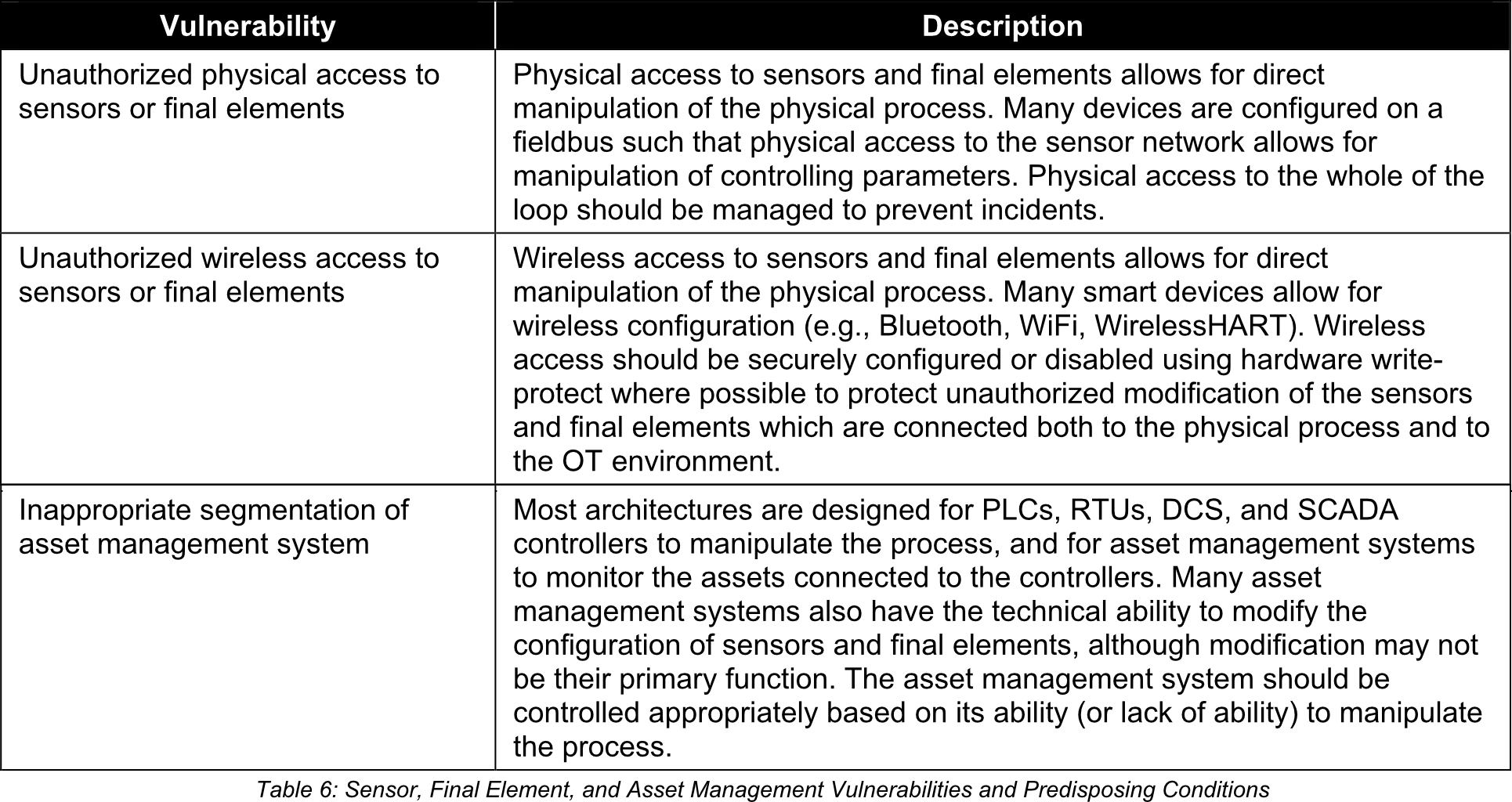
6. Sensor, Final Element, and Asset Management Vulnerabilities and Predisposing Conditions
As we presented the first two categories last week, today come the remaining ones
Physical Vulnerabilities and Predisposing Conditions
Software Development Vulnerabilities and Predisposing Conditions

Communication and Network Configuration Vulnerabilities and Predisposing Conditions
Sensor, Final Element, and Asset Management Vulnerabilities and Predisposing Conditions




0 Comments