
by Józef Sulwiński | 12 August 2021 | Blog-EN, Newest post
Eugene Wypior Small Business Cyber Resilience Improvement Guide. Part I – Introduction Introduction With the recent increase in ransomware attacks around the world the question shifts from “If we will get hacked” to “When will we get...
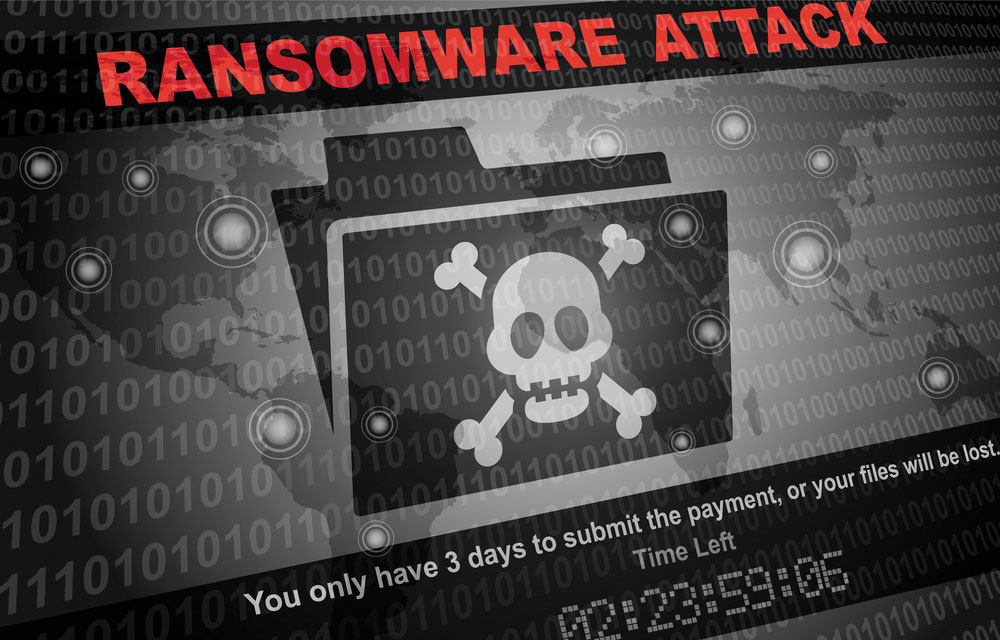
by Anna Krukowska | 15 December 2019 | Blog-EN
Seqred You sit down to your computer, drink your morning coffee, and … a multi-colored window is displayed on the monitor informing that your data has been encrypted, and only a cryptocurrency deposit on the given account will allow you to recover it. All...

by Anna Krukowska | 15 December 2019 | Blog-EN
Michał Niwicki UPnP (Universal Plug and Play – plug it in and it works) is a protocol that allows direct communication between computers and network devices. It is used in dozens of home appliances and enables devices such as computers, printers, TV sets, WiFi...

by Anna Krukowska | 8 July 2019 | Blog-EN
Błażej Dusik Let’s imagine a zombie army, like those straight from the silver screen – a charging horde that only has one goal. This reference to a Hollywood production can help us later understand the type of threat a botnet poses and how large it could be – an army...

by Anna Krukowska | 27 June 2019 | Blog-EN
Jakub Dzieciątko A proper reconnaissance lays the groundwork for further offensive action during security testing. The ability to search for information and to organise it in the right way could determine whether the later stages of the process will be easy, or even...






