ENISA’s Threat Landscape Report 2022 – Part 4 – Malware

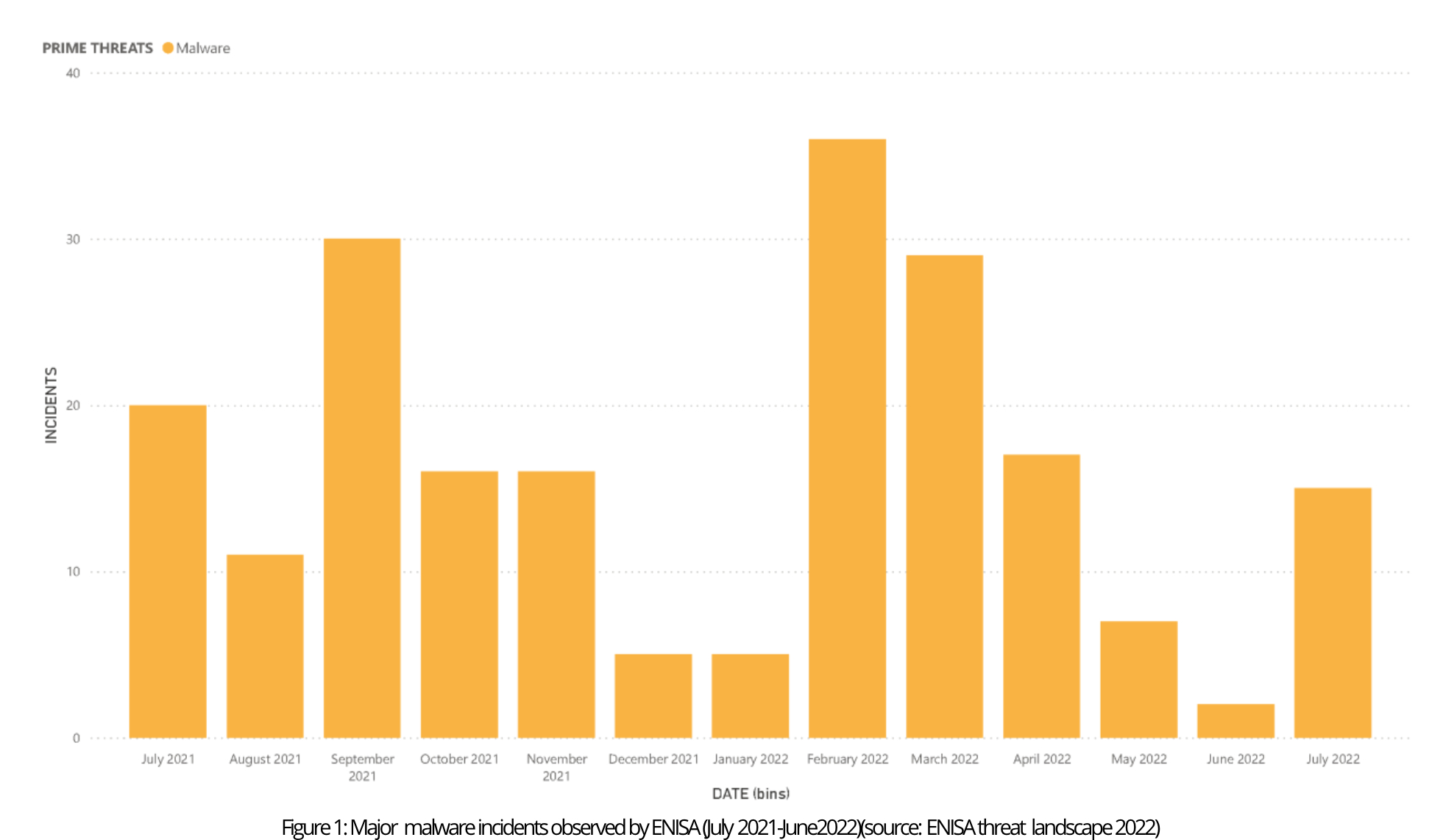
Malware trends
1. Malware detection on the rise after the COVID-19 drop
The global decrease in malware in 2020 and early 2021 was linked to the COVID-19 pandemic and remote work, limiting the visibility of malware on corporate infrastructures. However, there was a heavy increase in malware by the end of 2021, which is mainly attributed to crypto-jacking and IoT malware, and not linearly linked to more people being in the corporate environment.
In 2021, the most common malware families were RATs, banking Trojans, information stealers, and ransomware, with Agent Tesla, AZORult, Formbook, Ursnif, LokiBot, MOUSEISLAND, NanoCore, Qakbot, Remcos, TrickBot, and GootLoader being the most common strains, many of which have been active for over five years. This confirms that malware development is a continuous effort.
2. Malware targeting IoT almost doubles
In 2021, there was an increase in malware targeting IoT devices, which almost doubled in the first half of 2022 and was higher than in the previous four years. Mirai botnets were responsible for most attacks, quantified to more than 7 million, followed by Mozi, which was detected more than 5 million times. Networking devices such as Netgear (DGN), D-Link (HNAP), and Dasan (GPON) were the most common IoT targets in 2021 and 2022.
3. Supply chain attacks targeting open-source frameworks
Supply chain attacks are a means of distributing malware, whereby open-source frameworks are cloned and infected with malware, which can infect anyone who implements them as tools or packages in their projects. Since anyone can publish packages to open-source platforms, malware injection often goes unnoticed for a long time.
Attackers also use ‘typo squatting’ to introduce new packages in repositories with names similar to popular packages, increasing the likelihood of the package being referenced unintentionally or introduced by the attacker through a PR on the original project without standing out as an attack.
In 2021 and 2022, researchers found several malicious python libraries downloaded tens of thousands of times, which were used to steal information such as credentials, including pygrata and loglib. These attacks occur on popular repositories like NPM, Python, and RubyGems. An example of this type of malware is AsciI2text, which searches for local passwords and uploads them to the attacker’s infrastructure.
4. Shift away from Microsoft Office Macros
The use of VBA macros by malicious actors for deploying malware and ransomware has significantly declined since Microsoft’s announcement in July 2022 that Office applications would block macros in files from the internet. Instead, malware distribution campaigns have shifted towards using container files like ISO, ZIP, and RAR, and Windows Shortcut (LNK) files.
Between October 2021 and June 2022, the number of campaigns using VBA macros dropped from 70% to 20%, while the number of campaigns using LNK has risen from about 5% to over 70%.
For instance, in April 2022, a campaign utilized a zipped ISO attachment to deliver BumbleBee, a downloader equipped with anti-virtualisation checks.
It is important to note that many phishing campaigns employ password-protected archives to evade detection engines.
5. Mobile malware distribution: from broad infection to targeted attacks
Adware trojans were downloaded approximately 10 million times in June 2022, according to a report. Although Google has been quick to remove these malicious applications, they often go unnoticed for a considerable time. Adware functions by displaying invasive ads and attempting to subscribe users to expensive and premium services.
Targeted mobile malware has continued to be a significant threat during 2021 and 2022. In the previous reporting period, Pegasus, the NSO spyware was covered by the report, and since additional targeted attacks from other organisations have been observed, such as Predator from spyware developer Cytrox. Reports suggest that the targets of these attacks are frequently political opposition members, journalists, and activists.
6. Malware in the context of Ukraine
In January 2022, malicious activity was detected in Ukraine that involved the intrusion of Master Boot Records (MBR) Wiper. This malware was used against several organisations and disguised as ransomware, but it lacked the feature of data recovery. Its main purpose was to render systems and data inaccessible. Following this incident, numerous destructive malware strains, such as WhisperGate, HermeticWiper, IsaacWiper, HermeticWizard, and CaddyWiper, were discovered targeting Ukraine.
Cybercriminals also exploited the Ukraine-Russia conflict to lure victims into opening malicious attachments through malware spam campaigns such as Agent Tesla and Remcos.
Additionally, opportunistic attackers targeted Ukrainian sympathisers by hosting malware disguised as offensive tools to target Russian entities, which instead infected users upon download.
7. Coordinated take-down of mobile malware FluBot
Flubot is a type of mobile malware that spreads through text messages and targets Android users. The malware prompts users to click on a link and download an application. Once installed the application requests accessibility permissions, which allows the attacker to gain access to sensitive information such as banking credentials and cryptocurrency account details. Additionally, the malware disables built-in security mechanisms.
In June 2022, Europol announced that it had successfully taken down the Flubot operation and seized its infrastructure. The operation involved 11 countries, including Australia, Belgium, Finland, Hungary, Ireland, Spain, Sweden, Switzerland, the Netherlands, and the United States. The law enforcement agencies were able to gain control of the attacker’s infrastructure, which enabled them to determine the number of victims affected by the malware.




0 Comments