Defense in Depth strategies – Part 1

The days of physical separation between the corporate and operational domain, which together with the ‘security through obscurity’ approach were the main protective measures for ICS, are a tale of the past. Modern control system architectures, business requirements, and cost control measures result in increasing integration and interconnectedness of corporate and ICS IT architectures.
The advantages of this shift in ICS management are many, such as:
- New and more efficient methods of communication
- More robust data collection and aggregation methods
- Quicker time to market
- Interoperability
However, the integration of control system architectures with contemporary IT-based computing and networking capabilities introduces risks previously not encountered in isolated ICS. Applying the same technologies, that threat actors have already exploited and compromised on the Internet and in the corporate domain, increases the risk exposure of the ICS.
Defense in Depth – introduction
To improve the security of ICS, especially those responsible for the functioning of Critical Infrastructure, the IEC 62443 family of standards has been approved in 2021.
One of its concepts is the Defense in Depth approach to cybersecurity in Operational Technology.
The Defense in Depth concept originates from the military strategy and its aim is to create barriers that will slow down the advances of an intruder from attaining their goals while monitoring their progress and developing and implementing responses to the incident in order to repel them.
Defense in Depth is a holistic approach that protects all assets, using an organisation’s available resources to provide effective layers of monitoring and protection based on the business’s exposure to cybersecurity risks.
In order to apply Defense in Depth to the ICS environment, an organisation must understand the relationship between threats and vulnerabilities to the standards and countermeasures put in place to protect the operations, personnel, and technologies that make up an ICS.
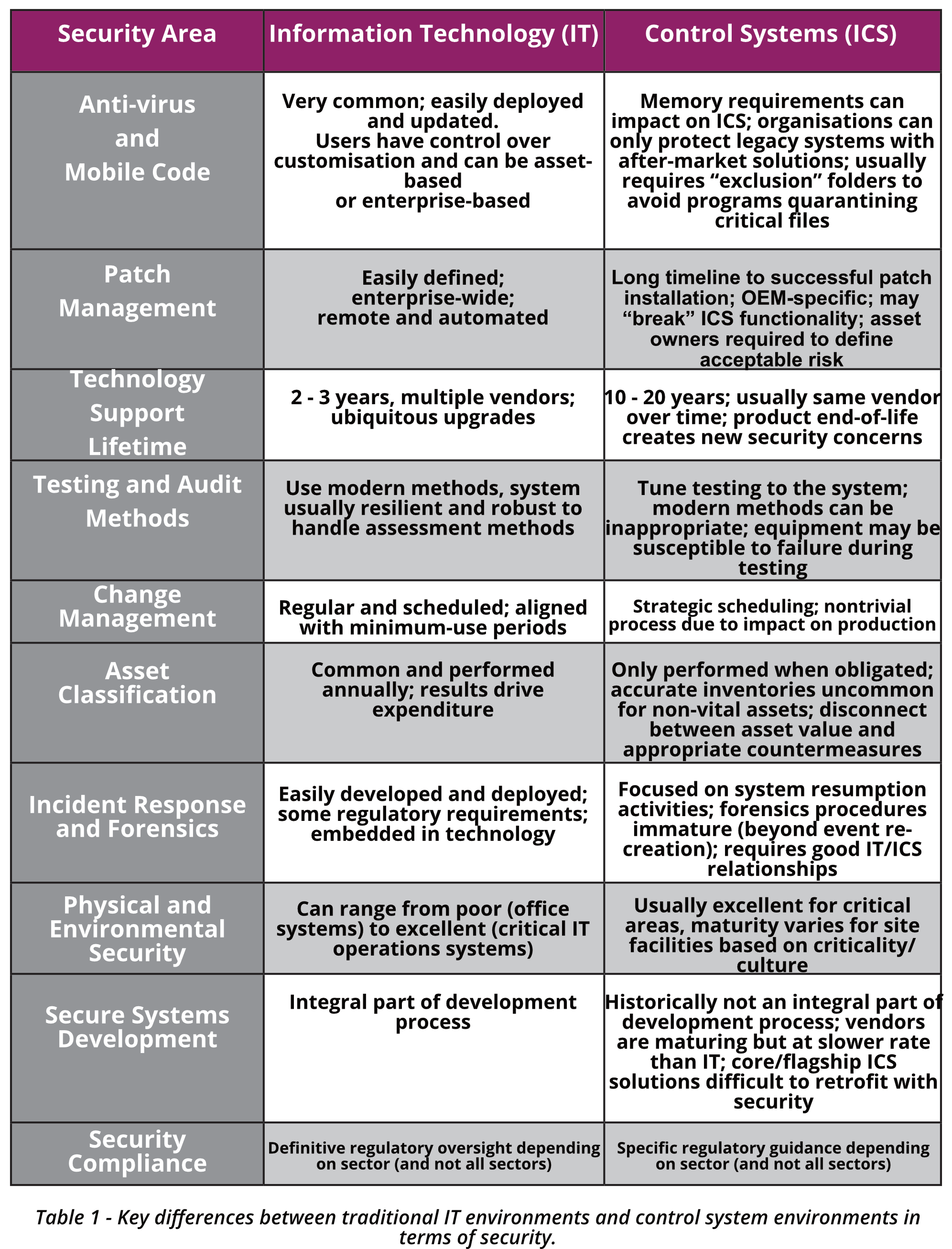
These security countermeasures protect ICS critical assets through multiple layers of defense. It is important to point out, that there are a number of key differences between traditional IT environments and control system environments in relation to security as presented in the below table.





0 Comments