Cybersecurity of Smart Buildings

When the topic of cybersecurity in Smart Buildings comes up, the question arises about the challenges related to the trend and technology, and who should be concerned about the topic.
Building owners, investors, building managers, tenants, as well as building users should be concerned.
Modern buildings are equipped with cutting-edge technology which is focused on making buildings more efficient by providing cost-saving solutions and bringing more value to the users via increased ease of use and comfort. Before we even realised these buildings became alike complex IT systems.
Example of Burj Califa

To bring it into perspective – the Burj Califa, with only 172m short of 1km, is the tallest building on earth at the time of writing this post. When you look at the building, what you see and what you imagine is probably the hundreds of thousands of tons of concrete and steel rebars. But have you ever asked yourself this question: “How many computers and computerised devices are needed to actually operate this building on a daily basis?” And we don’t mean the computers or machines used by tenants or businesses residing in the building but the equipment that is required to run the building such as systems that ensure that the doors to the building open and close as required.
There are around 1000 computerised devices including controllers, sensors, etc., and all of them are connected by a network used by the building. To give you a reference point – the data centre of a medium to big size European bank with around 20 million customers is equipped with 1000 servers. So, the complexity of Burj Califa is comparable to the complexity of the IT environment of a large European bank.
One must be aware that the solutions used in the building automation domain, use technology standards designed twenty or thirty years ago without security in mind.
Why is this important?
In the past, this technology was locked in the basements without access to the internet. Systems were operated by designated people, so vendors and technology users weren’t concerned about the security issues.
What happens twenty years later?

The same solutions and the same security technology standards are now used in the devices which are now connected to the internet. This can be compared to an open invitation for hackers saying “Hey there! I am a new device on the internet, why don’t you try to hack me.” And in many cases, hackers accept this kind of invitation out of curiosity, because of some benefits they want to gain, and in many cases, they like the challenge.
What is at stake for the victims of these types of stakes?
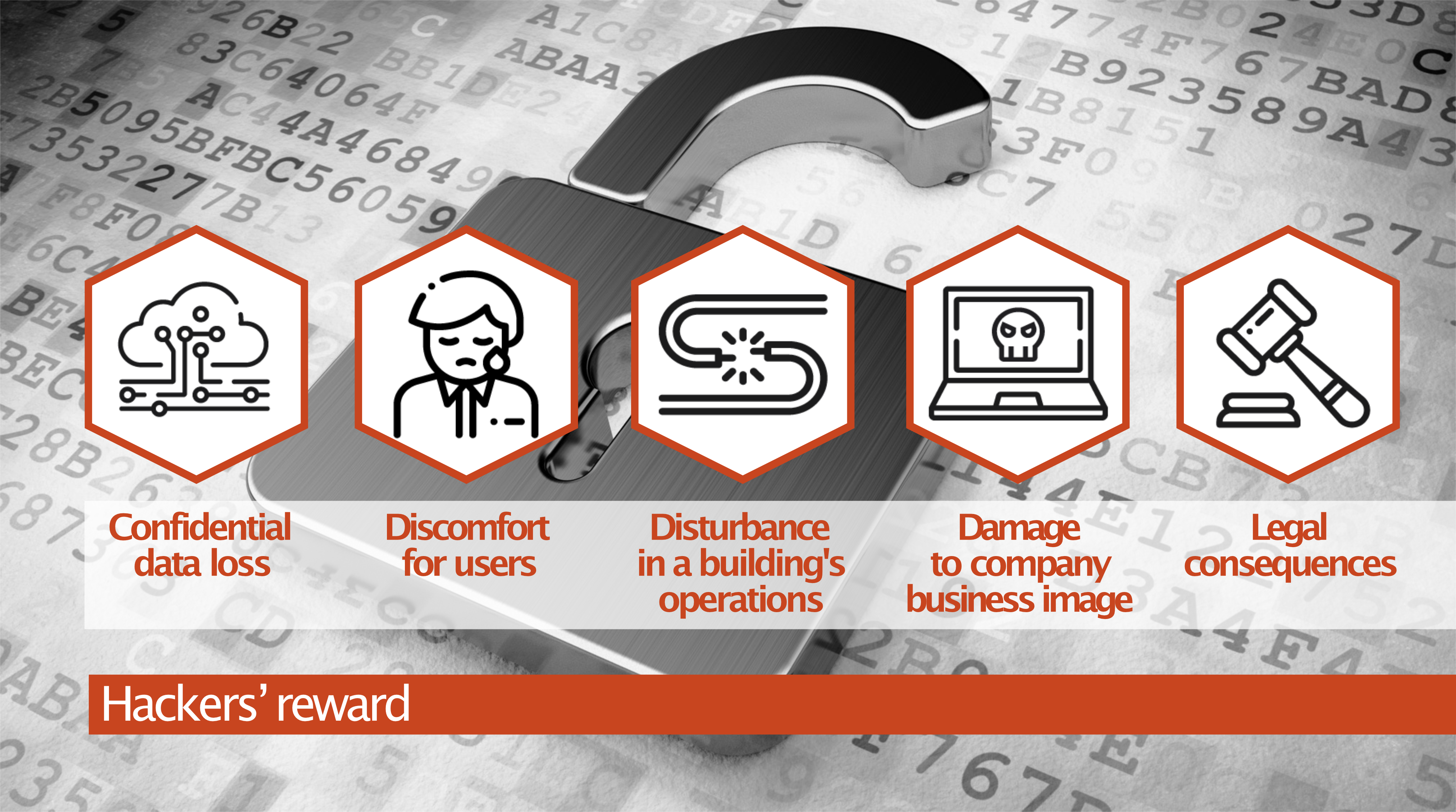
Loss of confidential data – it is not uncommon that those building controllers process and manage the information about the users of the building.
Discomfort for users – you can imagine the difficulty in using the building if the hacker locks the gates, and remotely alters the temperature in the rooms.
There is also the damage to the business image and legal consequences – nobody wants to be mentioned in an article about a serious security incident.
And what is the reality?
In 2017 a four-star hotel in Austria was subject to a ransomware attack. Ransomware was installed on the computer managing the building and as result, the system installed on this computer couldn’t be used. The direct operational consequences were such that the hotel guests could neither check in nor check out nor access their rooms. This resulted in a negative impact on the image of the company as well as financial losses.
In 2018 a similar type of ransomware attack was executed on 13 hospitals in the USA. The hospitals were unable to use part of their facilities and these circumstances were a life-threatening situation.
How big is the problem?
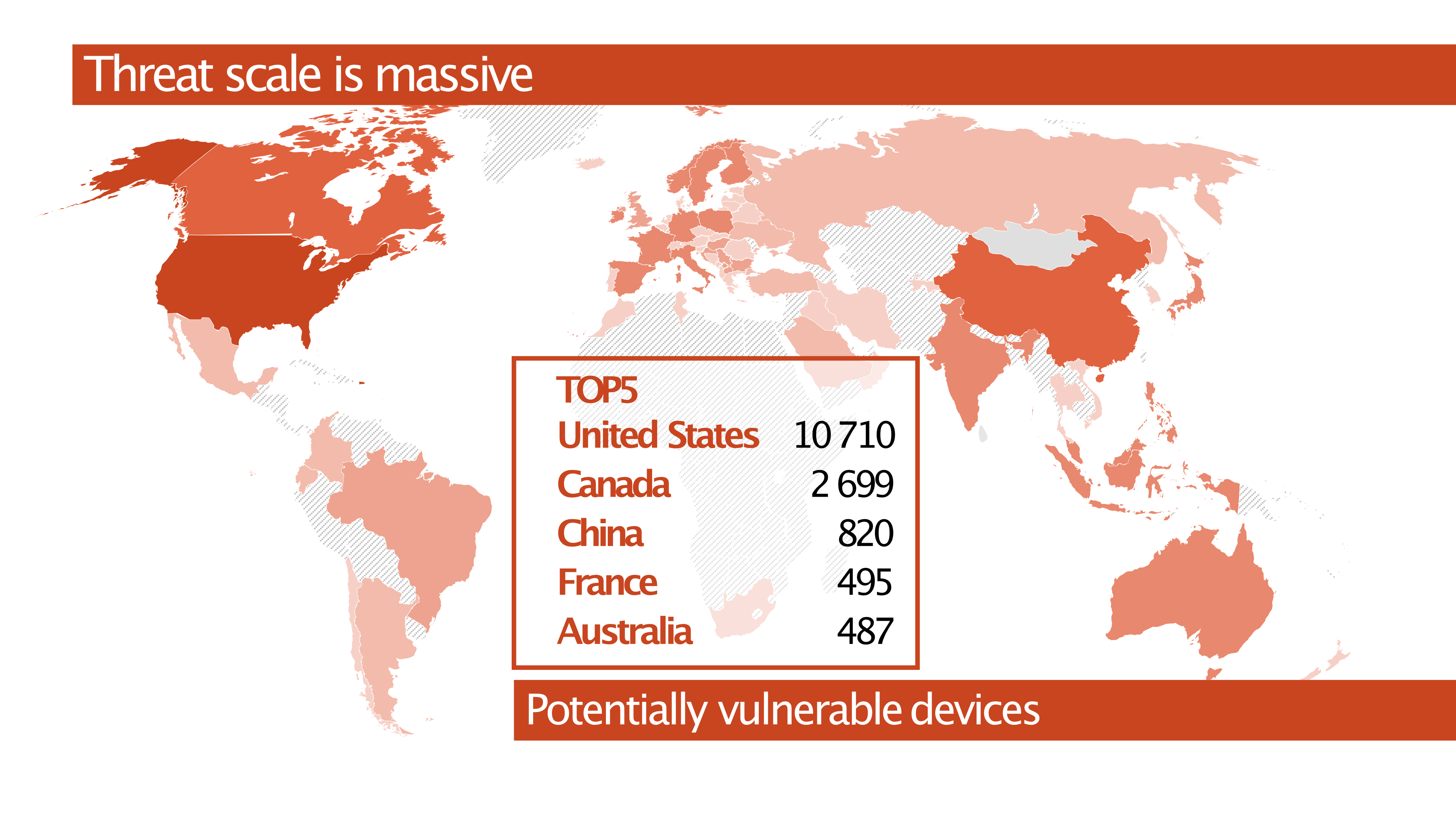
At SEQRED we use tools that are freely available online and we know for a fact that they are used by hackers too to collect information about IoT and OT devices including building controllers connected to the internet. When you use a proper combination of queries you are able to find thousands of Smart Building devices online. Not all of them are easy to crack, however, the hotel hack example shows that security flows exist and can be exploited.
Can this risk be mitigated?
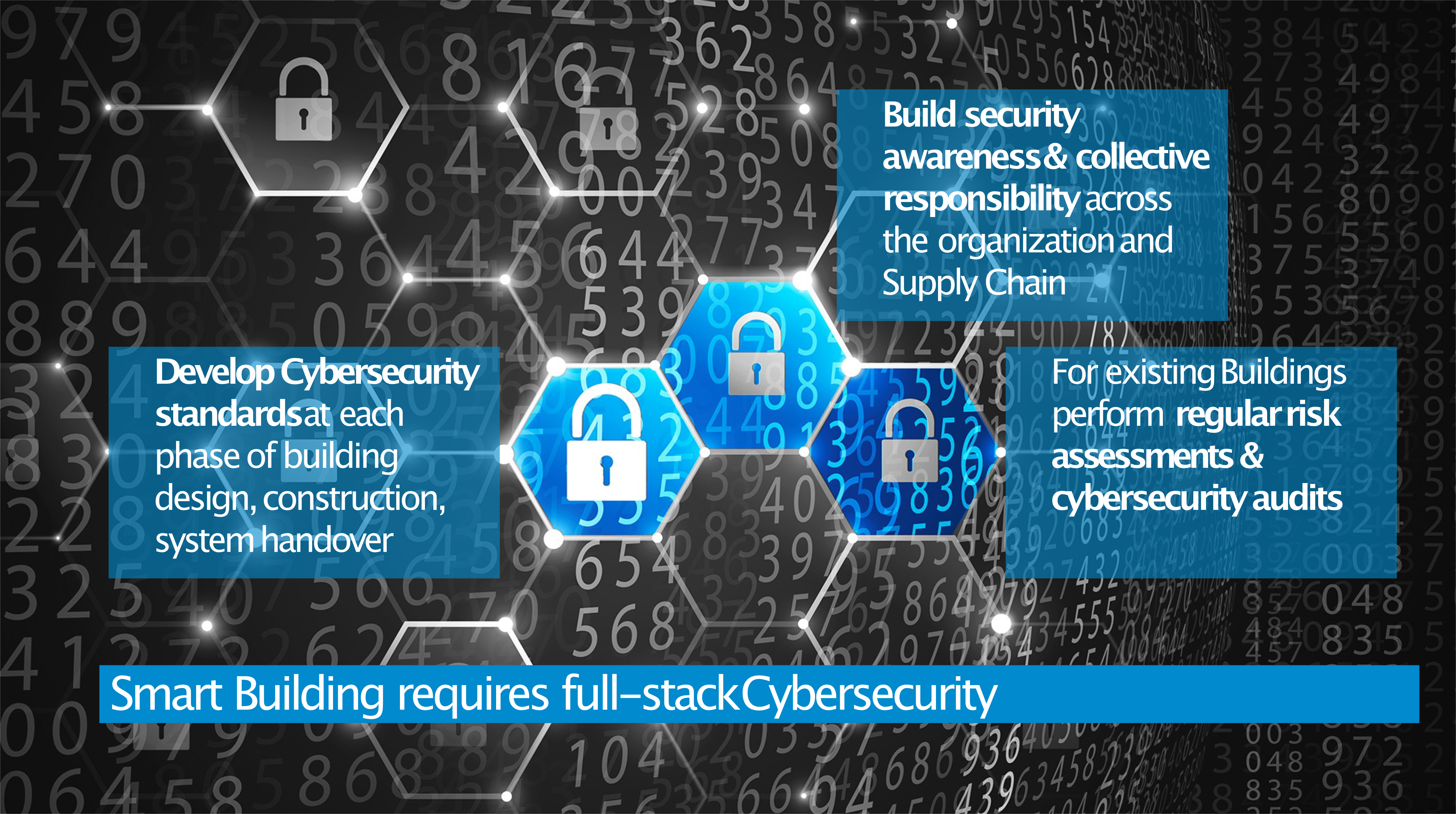
There are already certain behaviour patterns available that can be helpful. If you consider buildings as IT systems, you can adapt methods of managing IT projects – you should design and test security on each of the stages of the building construction project. After the construction is completed and the building is handed over to its managers and users it should be subject to periodical security audits because the technology risk profiles, including methods used by hackers, change over time, sometimes even daily.






0 Comments