Bring Your Own Device Security Strategies – Part 6

In today’s post, we continue with the
Deployment approaches
for BYOD
Bootable OS from a removable medium
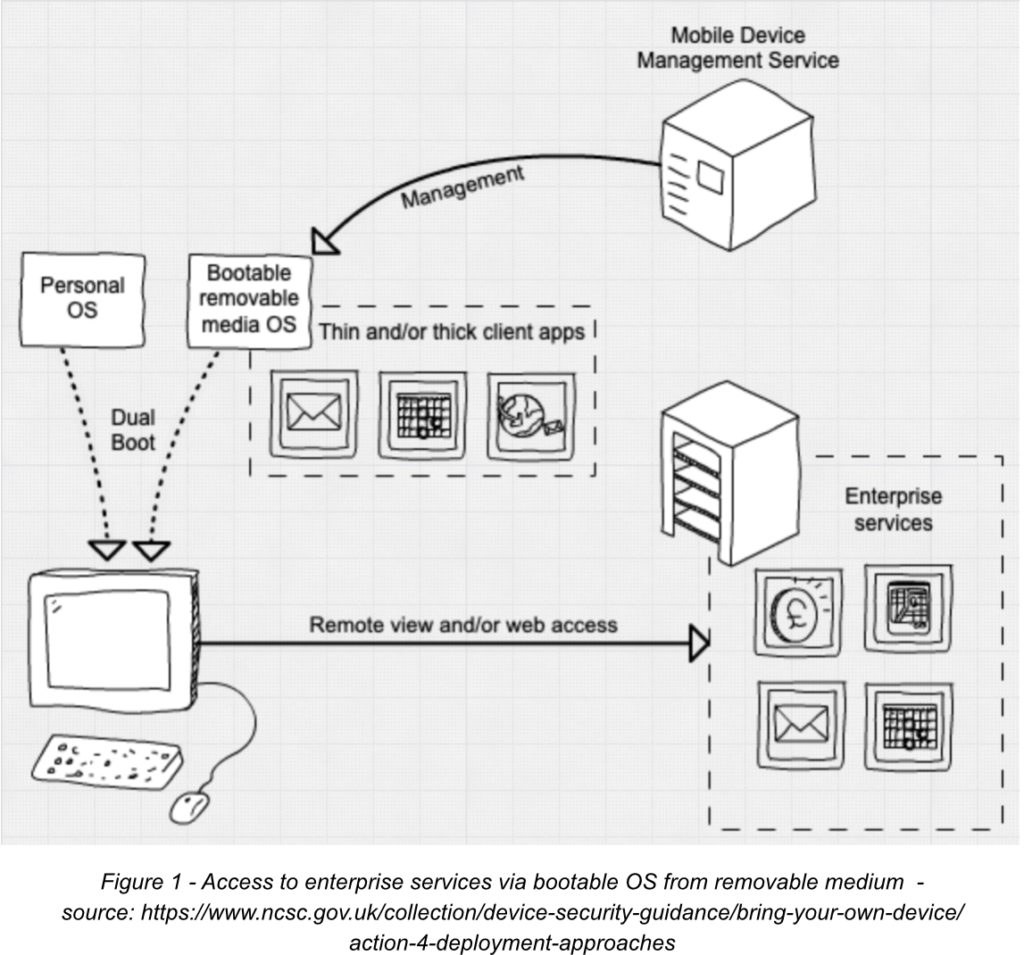
A low-risk way of enabling home PCs to be used for BYOD deployment is the use of a managed corporate environment booted from a removable bootable medium (such as a pen drive).
The advantage here is that the enterprise can manage the applications available to the device when furnishing the user with the bootable medium.
There are two main disadvantages to this solution.
Firstly, it is a fairly complex setup that is very likely to include a reconfiguration of the user’s device’s firmware.
Secondly, the underlying hardware of the device can be still vulnerable to attacks and is beyond the influence/control of the enterprise.
The technical controls available here include:
- Ensuring corporate data is stored in the correct repositories
- Using full volume encryption to protect from compromise or theft
- Keeping bootable OS images up to date
- Following all vendor’s best practices to limit the possibility of incidental data leakage
Mobile Application Management (MAM)
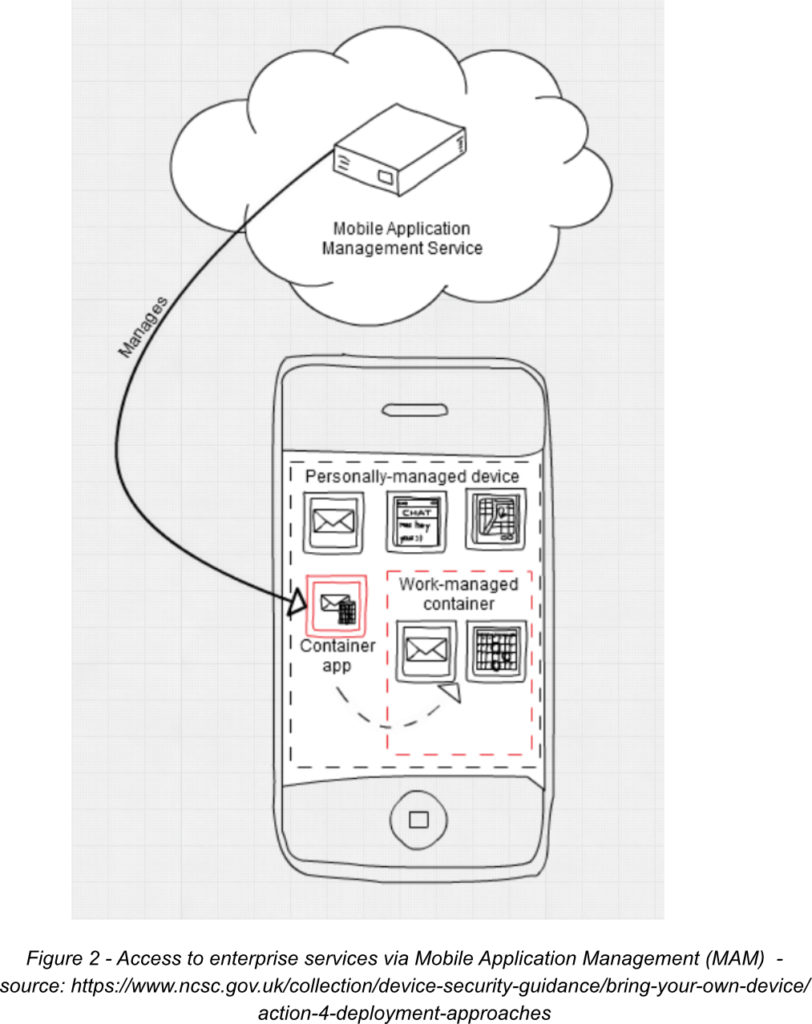
In this deployment type, the user manages all aspects of the device except for work applications. These are held within a container on the device and managed by the enterprise which has ownership of the data and resources within these containers. Corporate administrators can push settings to MAM-enabled apps which the user has installed within the container as well as put restrictions on the transfer of data out of the containers
This is an appealing solution for the user as there is a division between work and personal security controls.
PIN requirements can be enforced to unlock corporate apps and authentication and access control checks can be applied.
The security of this approach depends fully on the proper configuration of the apps used.
A further security concern is if the device itself gets infected with malware or otherwise compromised, it can spoof information to the managed app or gain access to corporate and personal data, and security tokens. This could happen if apps downloaded by the user were infected at the time of installation, which is possible in the case of MAM-WE (Mobile Application Management without Enrolment).
The controls available here to increase security are:
- Only access to enterprise services/applications from corporately managed/approved application stores should be allowed
- Using strong authentication for access to enterprise applications
- Enforcing app version compliance and pushing updates where possible
- Limiting the possibility to copy data from corporate apps to non-corporate apps
- Enabling remote removal of access to corporate applications and relevant data
In next week’s blog, we will look at more deployment approaches for BYOD.





0 Comments