Blog
Blog
How to enable multi-factor authentication in Office 365
The coronavirus pandemic has forced many organisations to undergo a rapid digital transformation and switch to a remote workforce. This sudden change created a need for tools allowing users remote access to company resources. Within a couple of days,...
Cloud computing security – identity and access management comparison for GCP and AWS
Cloud computing is the foundation of many digital transformation projects. Currently, enterprises see progressively more value in the ability to scale the cloud environment, being able to transfer part of the responsibility for reliability onto a cloud...
Can Building Management Systems be Potential Attack Vectors for Industrial Control Systems?
For many enterprises, working with advanced industrial systems the simultaneous implementation and use of Building Management Systems (BMS) is necessary. However, because their functionality is not seen as crucial for the realisation of the enterprise’s main...
CVE-2020-10551 – privilege escalation in QQBrowser
QQBrowser is a web browser developed by Tencent. It is one of the most popular web browsers used in China. During our tests, we have found a vulnerability which allows an unprivileged local attacker to gain code execution as NT AUTHORITY\SYSTEM. CVEID:...
OT and IT department cybersecurity – linked or separate?
In factories, companies and enterprises, cybersecurity for IT and OT departments should not be treated as separate issues. Historically, OT engineers have treated IT as a necessary evil, some of them even would go as far as “locking the infrastructure away”...
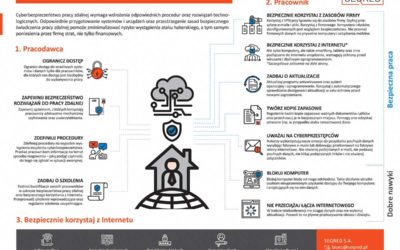
Best practices for safe and secure remote work
In order to ensure the cyber security of operations for staff working remotely it is vital to implement a number of appropriate procedures and technical measures. Adequate preparation of devices and systems used, as well as maintaining appropriate safety...
CVE-2019-14326 – privilege escalation in Andy
Andy is an Android emulator for Windows and Mac. During our tests, we have found open local TCP ports which could be exploited to escalate privileges from user to root. CVEID: CVE-2019-14326 Name of the affected product(s) and version(s): Andy (all versions...
Multiple vulnerabilities in Gurux GXDLMS Director – remote code execution
Gurux GXDLMS Director is an open-source Windows program for interacting with energy meters through the use of DLMS/COSEM protocol. The software has a remote update functionality for add-in DLLs as well as for files containing OBIS codes (device-specific...
CVE-2019-14514 – remote code execution in MEmu
MEmu is an Android emulator for Windows. During our tests, we have found an open TCP port which could be exploited to gain code execution with root privileges. CVEID: CVE-2019-14514 Name of the affected product(s) and version(s): Microvirt MEmu (all versions...
How to safely use removable media in ICS networks?
It's been 10 years since the alert issued by Cybersecurity and Infrastructure Security Agency (CISA) indicating the risks associated with using USB media as one of the sources of threat to control systems. Despite the passage of years, these threats still...