Bring Your Own Device Security Strategies – Part 7

In today’s post, we continue with the
Deployment approaches
for BYOD
Mobile Device Management (MDM)
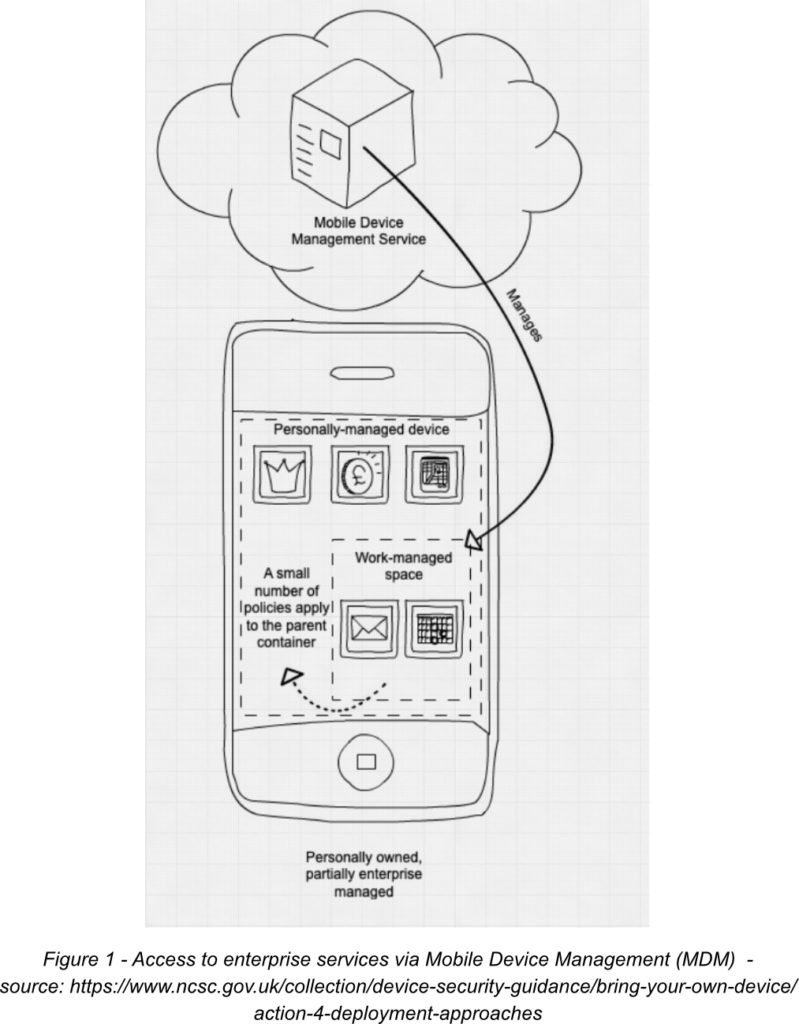
The approach of Mobile Device Management (MDM) for Bring Your Own Device (BYOD) involves enrolling personal devices into a corporate system that grants the enterprise a certain amount of authority over the device and its settings. This method is usually referred to as “partially managed.” All device systems including iOS, macOS, Android, ChromeOS, and Windows 10 are compatible with MDM, each providing different levels of security.
MDM software works with the specific device to apply its security controls, so the management capabilities will depend on the device and platform. Often, MDM software is part of an Enterprise Mobility Management (EMM) suite. MDMs are typically able to enforce some device–wide configuration policies and policies that protect corporate data within apps or managed accounts. Mobile Application Management (MAM) functions in a similar way.
Using this solution can provide greater assurance of device security, but the degree of control over the device may be worrying to the owner, making this a less popular choice.
MDM Security controls
Security tokens of services being accessed can be accessed by malware running with privilege on a compromised device, either through escalation on an unpatched device or through a user running as a privileged user. This can undermine the security controls implemented and enforced at the platform level (usually in kernel mode by MDMs.
Cached data may also be exposed.
Some of the advantages of MDM include:
- Access control policies can be set up so that a device must be registered, and its settings, patch status, and anti-malware protection must meet the policy requirements
- Can ensure that the device and browser are kept up to date by prompting the users to install the latest updates
- Encourage users to download work apps from the company‘s app store.
The main downside of this solution it that the integrity of the underlying platform generating data used to enforce security controls is essential; if it is sufficiently compromised, it could provide false information to the managed app, thus weakening security controls.
There are several technical controls available to enforce the BYOD policy in this deployment style. Some of them are:
- Installing apps from approved lists using enterprise app catalogs
- Making sure access to corporate assets can be remotely restricted
- Limiting the ability to copy data between work and personal settings
- Granting access only to corporate resources that the user needs.
Hybrid Approaches
Some vendors offer a hybrid of MDM and MAM, which is typically part of an MDM, UEM (Unified Endpoint Management), or EMM (Enterprise Mobility Management) suite.
This setup enables partial device management and stores most of the work data within a container, which can help reduce the risk of using container applications. However, it may also require users to accept more enterprise control over their devices.




0 Comments