Threat Sources, Vulnerabilities, and Incidents – part 1

Several terms are used to describe the inter-related concepts of threat, threat source, threat event, and incident. A threat is any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the Nation through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service. Threats have some intent or method that may exploit a vulnerability through either intentional or unintentional means. This intent or method is referred to as the threat source. A vulnerability is a weakness in an information system (including an OT), system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source. A threat event is an event or situation that has the potential for causing undesirable consequences or impact. When a threat event occurs it becomes an incident that actually or potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.
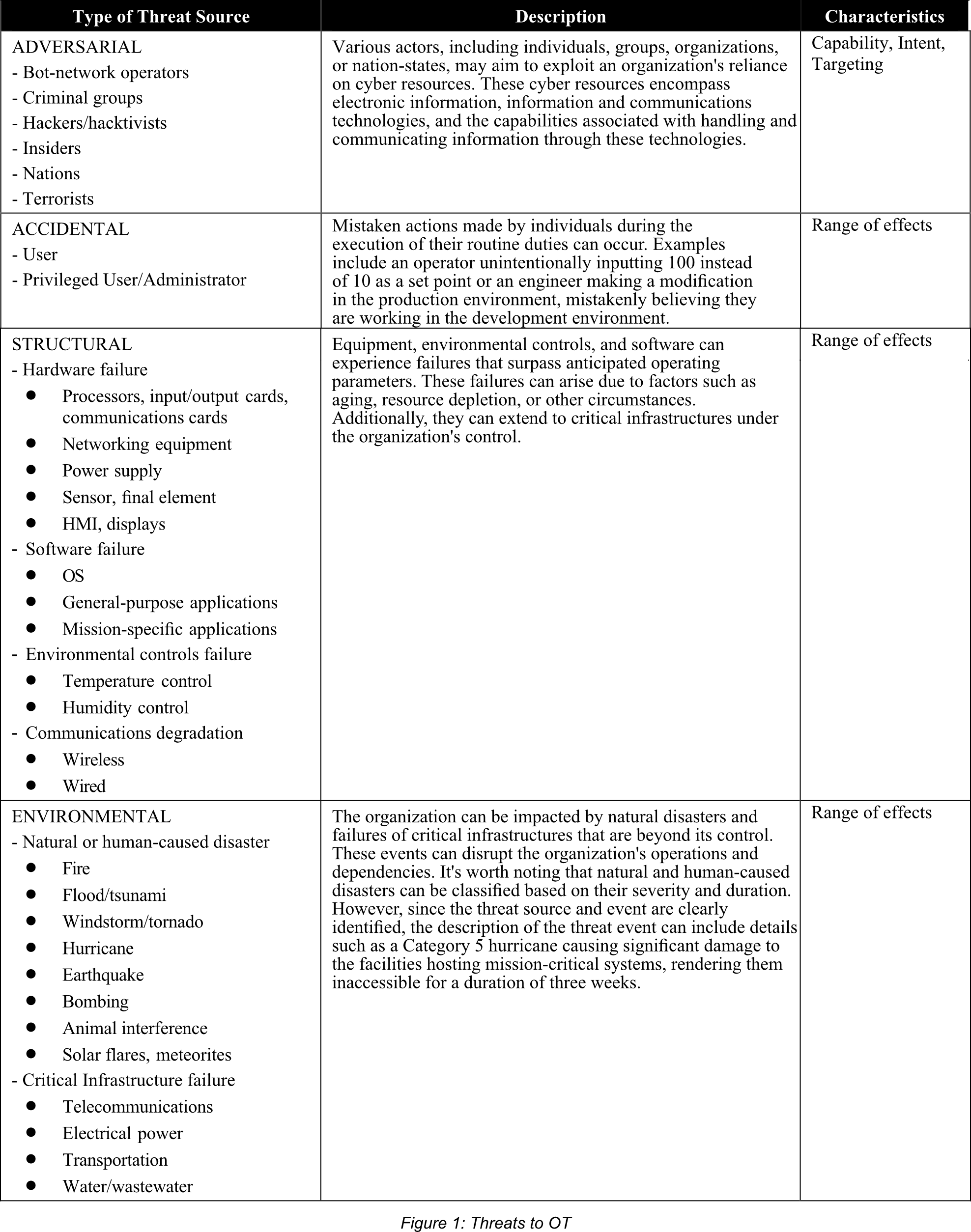
Threat Sources
OT systems face a wide range of potential threats, originating from various sources that can be categorized as adversarial, accidental, structural, or environmental. These diverse threat sources must be incorporated into the overall risk management strategy. Understanding the nature of each threat source is essential to effectively define and deploy appropriate protective measures.
For instance, environmental events like floods or earthquakes are generally familiar to us, but their impact can differ significantly in terms of severity, frequency, and potential to exacerbate other interconnected incidents. On the other hand, adversarial threats are contingent upon the resources accessible to the adversaries and the discovery of previously unknown vulnerabilities or attack methods.
To ensure the security of OT systems, it is crucial to comprehensively evaluate and address threats emanating from different sources. This involves developing a comprehensive understanding of each threat source and implementing suitable protective measures accordingly. By doing so, organizations can mitigate risks and enhance the resilience of their OT infrastructure.
Vulnerabilities and Predisposing Conditions
Vulnerabilities refer to weaknesses present in information systems, system procedures, controls, or implementations that can be exploited by potential threats. Predisposing conditions, on the other hand, are characteristics of the organization, mission/business processes, architecture, or information systems that contribute to the likelihood of a threat event occurring. The order in which vulnerabilities and predisposing conditions are listed does not indicate priority in terms of likelihood or severity. It is important to note that the provided list of vulnerabilities and predisposing conditions is not exhaustive, and not all OT environments will necessarily exhibit these issues.
These vulnerabilities and predisposing conditions are categorized based on their existence in the organization’s policies and procedures or in the inadequacy of security mechanisms within the system. Understanding the origin of vulnerabilities and predisposing conditions can help determine the most effective mitigation strategies. It is possible that deeper analysis may reveal that certain causes can exhibit multiple symptoms, and some symptoms may stem from more than one cause.
While some vulnerabilities and predisposing conditions can be mitigated, others can only be accepted and controlled through appropriate countermeasures, resulting in residual risk within the OT environment. For instance, certain policies and procedures may be modified within an acceptable level of effort, while additional policies and procedures may need to be implemented to address other issues promptly.
When it comes to products and services acquired from external sources, the organization has limited direct control over the vulnerabilities present. Changes in these areas are often influenced by market forces, which can be a slow and indirect approach. Instead, the organization may choose to modify predisposing conditions to reduce the likelihood of exploiting systemic vulnerabilities.
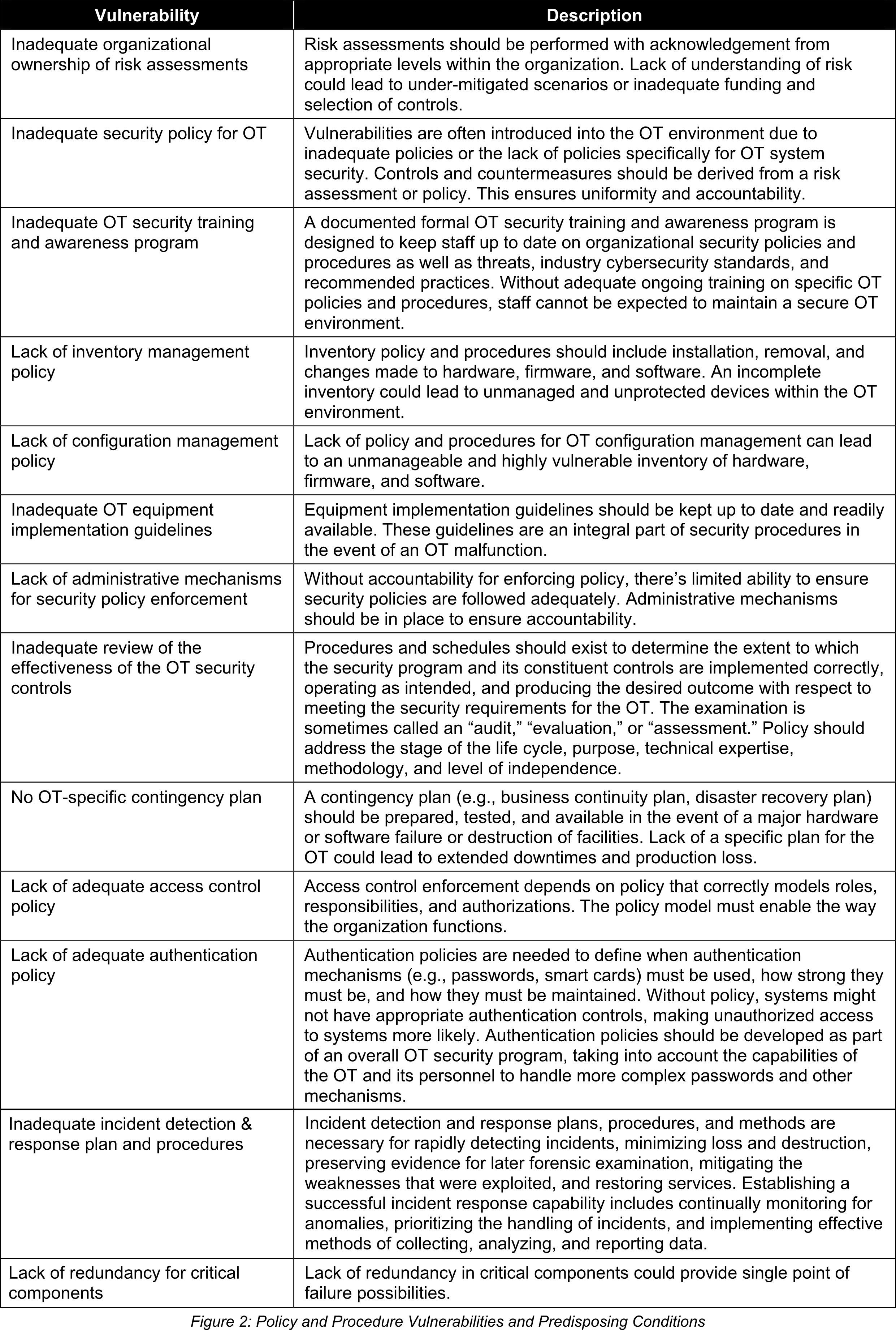
Policy and Procedure Vulnerabilities and Predisposing Conditions
Vulnerabilities and predisposing conditions frequently find their way into the OT environment due to inadequate, inappropriate, or nonexistent security policies. This encompasses the lack of proper documentation, implementation guides (such as procedures), and enforcement of security measures. The support of management is crucial as it forms the foundation of any effective security program. By establishing and enforcing security policies, organizations can minimize vulnerabilities by mandating appropriate conduct.
Written policies and procedures serve as essential mechanisms for informing staff and stakeholders about the organization’s decisions regarding behavior that benefits the organization. From an educational standpoint, policies provide guidance and instructions that help reduce vulnerabilities. Enforcement is a critical complement to policies as it motivates individuals to adhere to the expected protocols. Non-compliance with policies and procedures typically results in various forms of corrective action. Policies should explicitly outline the consequences for individuals or organizations that fail to conform.
The policy and procedure landscape is often complex, involving laws, regulations, overlapping jurisdictions, spheres of influence, economic factors, customs, and historical considerations. In larger enterprises, there are often organizational units that should collaborate to minimize vulnerabilities. Managing the scope and hierarchical relationship among policies and procedures is essential for maximizing their effectiveness.





0 Comments