Defense in Depth strategies – Part 9 – Security Monitoring

Security Monitoring
Putting in place a boundary around the ICS made up of devices, settings and procedures is essential but not sufficient to protect critical assets from unauthorised access, as for each protective device deployed there is a method devised by threat actors to overcome it.
According to the concept of Defense in Depth a system must be able to detect and alert an enterprise of an intrusion and it must be able to do so early enough so the enterprise can take defensive action before critical assets are breached.
Hence monitoring the ICS and its networks for changes, abnormal behaviour or attack signatures is an essential element of a cybersecurity setting.
There are many ways enterprises can monitor their networks and collect information, two of which are
Intrusion Detection and Prevention Systems
Despite considerable network traffic, that traffic is quite predictable – the various components of the ICS environment communicate in standardised ways. As result, an Intrusion Detection System can monitor and create alarms for any traffic outside normal operations in a relatively simple way by rules monitoring for IP sources and destinations, protocols, lengths of packets, etc.
Intrusion Prevention Systems can be placed in line with firewalls or ICS equipment and contrary to their IDS counterpart can take the action of blocking traffic that does not meet the required standards. Their use and settings, however, must be very well thought through as they can possibly stop a process and as result put operations to a halt. Therefore, they should be set to trigger only extreme anomalies.
An IDS is not limited to being only network-based. There are host-based IDSs (HIDS) that monitor the state of a computer and there are Application-Level Detection Systems (ALDS) monitoring the state of an application.
IDS sensors should be strategically located to obtain quality information. Traditionally they are placed in high-traffic locations and/or between security boundaries or networks with sensitive information.
Potential complications with using IDS/IPS include the fact that it takes a significant amount of work to write rules and requires thorough testing to ensure that the rules function properly.
Detection Methods Characteristics and Selection Considerations
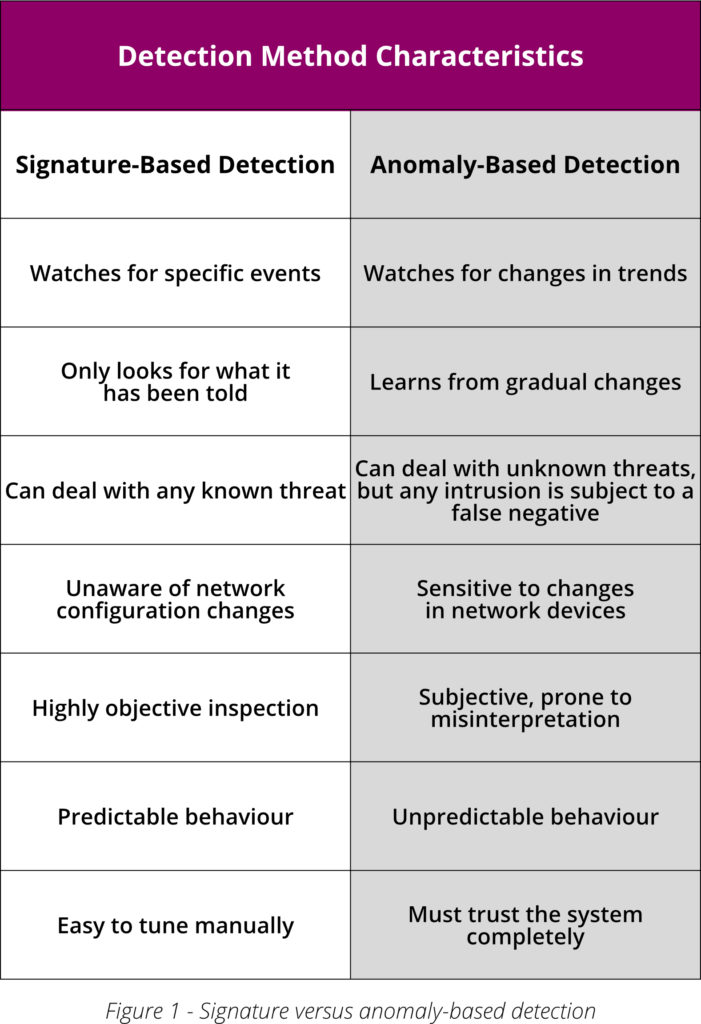
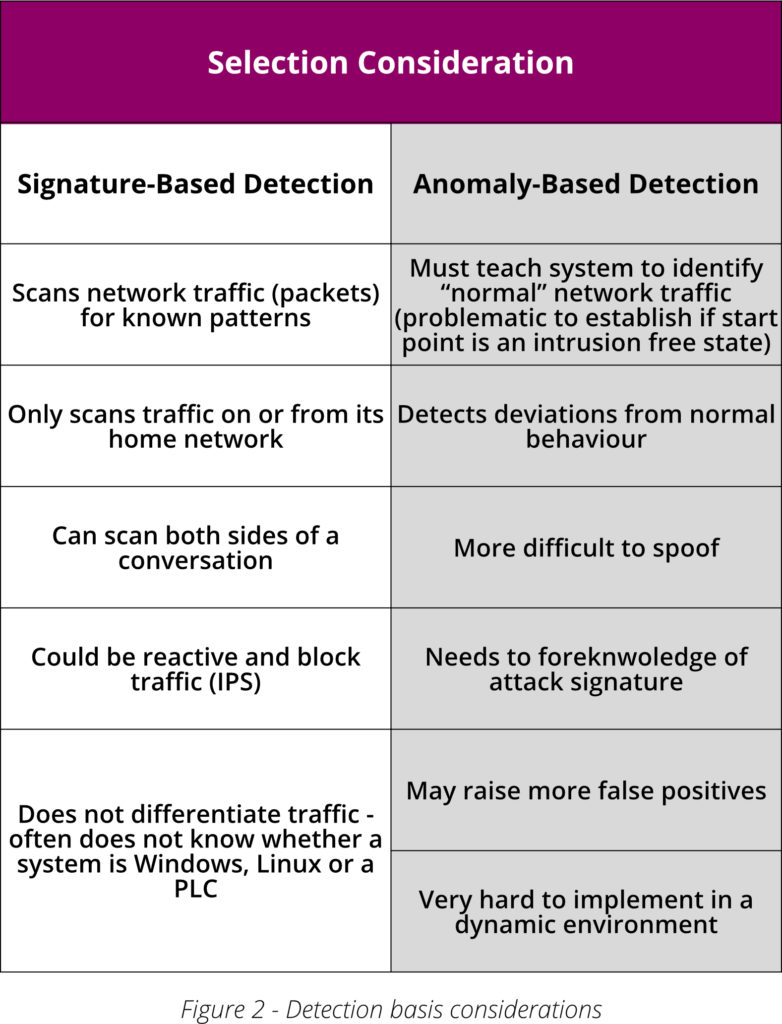
Signature-based and anomaly-based detections are the two main methods of identifying and alerting on threats. While signature-based detection is used for threats we know, anomaly-based detection is used for changes in behavior. Each has its own advantages and disadvantages.
Security Audit Logging
Security audit logs provide information about login activity, resource use, file modifications, and other security-relevant information. Properly configured audit logs at the network, host, and application levels provide critical information for determining how an incident occurred, the impact and scope of the issue, and how best to deter future events.
Comprehensive log management and analysis policies establish the minimum requirements for devices, operating systems, and applications. A baseline of expected traffic and process functionality for normal and off-normal operations and system use allows security, process control, and control systems operations personnel to isolate unusual data traffic or user actions that may indicate potential security-impacting events.
Security Incident and Event Monitoring (SIEM)
A SIEM centralizes data from network devices, operating systems, applications, and databases within complex environments, such as control system networks. It streamlines the audit log review process, by porting logs from multiple systems into one solution that eliminates the time and effort required for manual log reviews. Organizations can set up a SIEM to integrate multiple log formats from widely distributed sources and collect the information both remotely and automatically. The SIEM can also integrate IDS/IPS information and scanning results and generate alerts on identified traffic patterns. A SIEM’s analysis engine speeds up data processing and formatting time, making it cheaper and easier to review functional, operational, and security data. In addition, using a SIEM provides the ability to select specific events for compliance reporting, root cause failure analysis, and incident detection.





0 Comments