Cybersecurity Maturity Model Certification (CMMC) Program – Part 2

Cybersecurity Maturity Model Certification (CMMC) 2.0 is a certification framework implemented by the US Department of Defence (DoD) to protect the information and ingenuity pertinent to the national security of the US used in the process and for the sake of procurement by independent contractors.
Depending on the accessed and processed information contractors are required to acquire relevant level certification prescribed by the requirements and model of assessment.
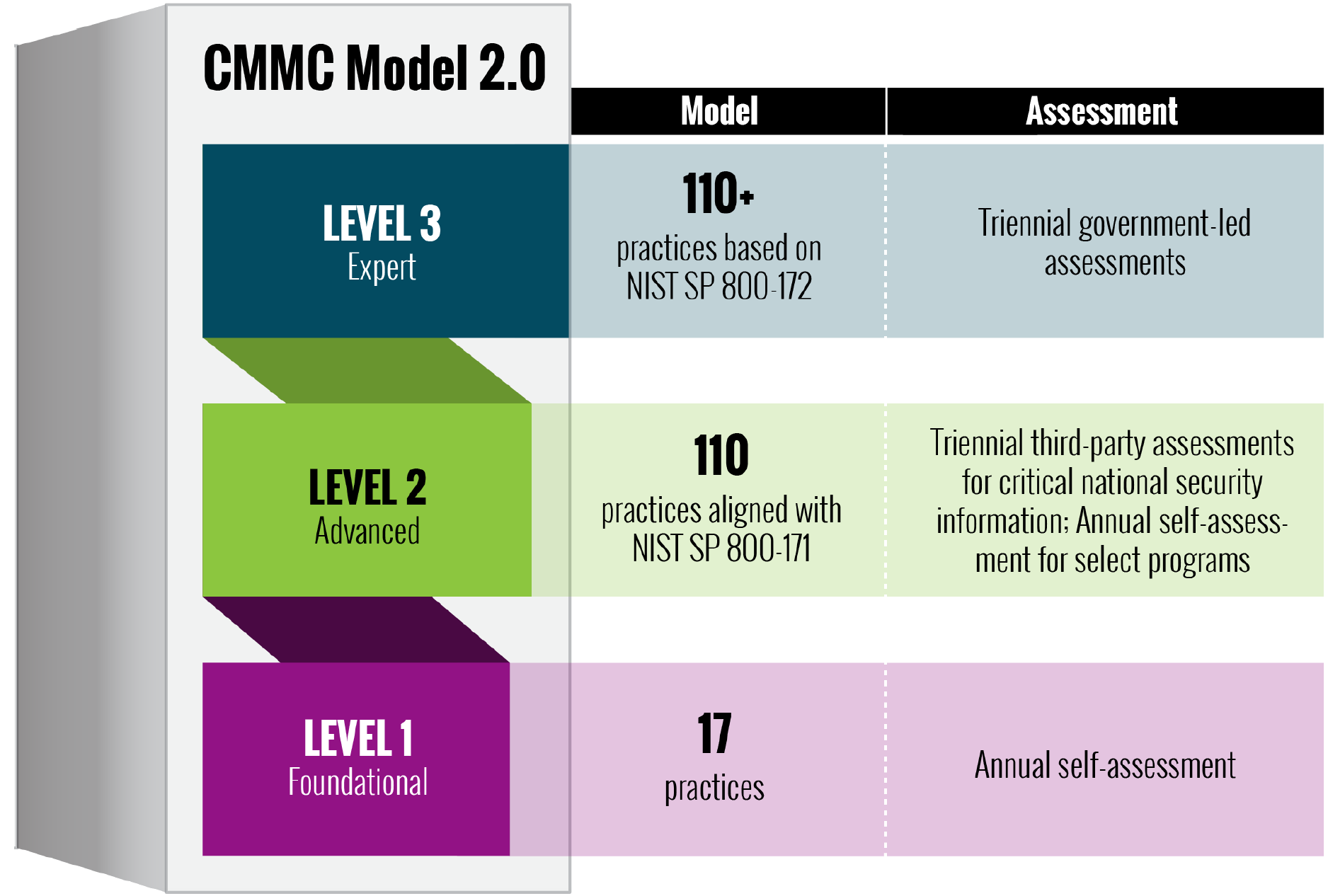
For Level 1 (Foundational) – assessment of the following areas is subject to audit:
- Resources/systems processing, storing or transferring the Federal Contract Information (FCI). It encompasses:
- People (employees)
- Technologies (servers, mobile devices, and applications)
- Office spaces
- Aligned with NIST 800-171 the following main areas of limiting access of IT systems, handling of data carriers, verification of physical access logs (e.g. from access control, separation, and segmentation of IT systems, implemented anti-malware system
- The full list of 17 practices consists of the following areas
- Access Control (AC)
- L1-3.1.1 – Authorised Access Control
- L1-3.1.2 – Transaction & Function Control
- L1-3.1.20 – External Connections
- L1-3.1.22 – Control Public Information
- Identification and Authentication (IA)
- L1-3.5.1 – Identification
- L1-3.5.2 – Authentication
- Media Protection (MP)
- L1-3.8.3 – Media Disposal
- Physical Protection (PE)
- L1-3.10.1 – Limit Physical Access
- L1-3.10.3 – Escort Visitors
- L1-3.10.4 – Physical Access Logs
- L1-3.10.5 – Manage Physical Access
- System and Communication Protection (SC)
- L1-3.13.1 – Boundary Protection
- L1-3.13.5 – Public-Access System Separation
- System and Information Integrity (SI)
- L1-3.14.1 – Flaw Remediation
- L1-3.14.2 – Malicious Code Protection
- L1-3.14.4 – Update Malicious Code Protection
- L1-3.14.5 – System & File Scanning
- Access Control (AC)





0 Comments