Cybersecurity Framework – Identify

Cybersecurity Framework in OT
The NIST Cybersecurity Framework (CSF) has been widely adopted by various organizations in both the public and private sectors. It serves as a guide for conducting cybersecurity activities and addressing cybersecurity risks. This framework encompasses five interconnected and continuous functions: Identify, Protect, Detect, Respond, and Recover. These functions present industry standards, guidelines, and practices in a way that facilitates communication about cybersecurity activities and outcomes throughout the organization. Together, they offer a holistic and strategic approach to managing cybersecurity risks.
The functions of the CSF provide guidance for the following actions:
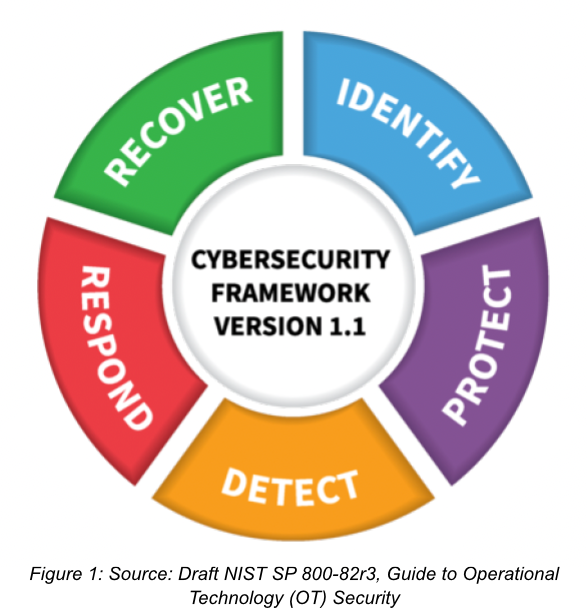 |
Identify (ID) – Establish a comprehensive understanding of the organization’s cybersecurity risks, including systems, personnel, assets, data, and capabilities. Protect (PR) – Create and enforce suitable safeguards to ensure the uninterrupted delivery of critical services. Detect (DE) – Establish and execute appropriate measures to identify cybersecurity events as they occur. Respond (RS) – Develop and implement suitable actions to address detected cybersecurity incidents promptly. Recover (RC) – Develop and implement effective strategies to restore impaired capabilities or services and maintain resilience in the face of cybersecurity incidents. |
IDENTIFY
The Identify Function plays a fundamental role in utilizing the CSF effectively. Its primary objective is to establish a comprehensive organizational understanding that enables the management of cybersecurity risks pertaining to systems, individuals, assets, data, and capabilities. The desired outcome of the Identify Function is to foster a robust awareness and comprehension of these risks for effective risk management.
Asset Management
The capability for organizations to identify and manage data, personnel, devices, systems, and facilities based on their respective importance is a critical foundation for supporting an organizational cybersecurity program accurately and consistently. Furthermore, regularly updating inventory information when changes occur (such as adding or removing components, applying patches, installing new firmware, or swapping components during maintenance) assists organizations in effectively managing risks within their overall environment. To enhance their asset management capability, organizations should consider incorporating the following elements:
Unique identifiers to differentiate and track assets
- Managing hardware inventory to monitor computing and network devices present in the environment, encompassing comprehensive device information and their whereabouts. Device details may encompass vendor information, model specifications, serial numbers, purchase records, and manufacturing/build data (such as provenance information).
- Administering software and firmware inventory to monitor the installation of software and firmware on OT components. This includes tracking version numbers, location information, Software Bill of Materials (SBOM), and other relevant details.
- Compiling vendor information to establish a centralized repository containing details about vendors, points of contact, warranty information, recall and update locations, and other relevant data.
- Creating documented roles and responsibilities to identify individuals, teams, or organizational groups responsible for representing the asset owner, as well as those fulfilling operation and maintenance duties, and cybersecurity roles and responsibilities.
OT-Specific Recommendations and Guidance
Organizations should prioritize the importance of maintaining a complete and accurate asset inventory to effectively manage risks within the Operational Technology (OT) environment. Having precise inventory information serves multiple risk management objectives, such as conducting risk assessments, managing vulnerabilities, and tracking obsolescence.
While automated tools are generally preferred for asset management, organizations need to assess how these tools collect information and determine if the collection method, such as active scanning, might adversely affect their OT systems. It is advisable to perform a test using automated asset management tools on offline systems or components before deploying them in the live OT production environment. In cases where automated tools are not feasible due to network architectures or other issues specific to the OT environment, organizations should consider implementing manual processes to ensure the inventory remains up-to-date.
Mapping Data Flows
Data flow diagrams provide manufacturers with a visual representation of how data moves between interconnected components within a network. By documenting these data flows, organizations gain a clear understanding of the expected behavior of their networks. This comprehension of device communication assists in troubleshooting, as well as response and recovery efforts. Moreover, this information proves valuable during forensic activities and analysis, enabling the identification of anomalies and facilitating effective incident response.
OT-Specific Recommendations and Guidance
When utilizing automated data flow mapping tools for Operational Technology (OT) systems, organizations must carefully consider the potential impacts. Tools that employ active scanning or require network monitoring tools (such as in-line network probes) may have consequences on OT systems. These impacts could arise from the sensitivity of the information being accessed, the volume of network traffic generated, or the momentary disconnection of manufacturing system components from the network.
To mitigate these risks, organizations should contemplate employing data flow mapping tools that utilize these methods during planned downtime. By selecting an appropriate timing, organizations can minimize disruptions and potential negative effects on OT systems while still benefiting from the valuable insights provided by the data flow mapping process.
Network Architecture Documentation
Network architecture documentation tools facilitate the process of identifying, documenting, and visualizing the interconnections among networked devices, corporate networks, and external connections. Having a thorough comprehension of these interconnections is crucial for the successful implementation of cybersecurity controls. Equally significant, this information plays a vital role in enabling effective network monitoring.
OT-Specific Recommendations and Guidance
Network architecture documentation tools that employ automated topology discovery technologies are limited to capturing information solely from IP-based networked devices. However, in many operational technology (OT) environments, there exist isolated systems, components, or systems connected through non-IP networks. Consequently, these OT environments may not possess the technical capability to utilize automated network architecture documentation tools. In such cases, manual processes become necessary for documenting these components.
Asset owners should consider the potential impact of automated scanning activities on the OT system and consider testing automation tools in a non-production environment. Based on the results of these tests, asset owners can make informed decisions about employing automated OT network architecture documentation tools during scheduled downtime.
Furthermore, organizations may opt to conduct physical inspections of OT network connections or analyze network logs as alternative approaches to document the OT network architecture, particularly when the network is relatively small or uncomplicated. By incorporating OT network activity monitoring, organizations can identify any addition or removal of devices within the environment between planned scanning activities.
Governance
Achieving effective governance entails organization leadership integrating risk management objectives, as well as resiliency, privacy, and cybersecurity objectives, into the strategic planning process. This integration involves providing the necessary resources to efficiently implement and maintain the cybersecurity program. Through this inclusive process, organization leadership formulates and communicates policies that establish security requirements for their environments.
These policies encompass various elements, such as the identification and allocation of roles and responsibilities, management commitment, and compliance. Additionally, the policies may reflect coordination among different organizational entities responsible for distinct security aspects, including technical, physical, personnel, cyber-physical, access control, media protection, vulnerability management, maintenance, and monitoring.
OT-Specific Recommendations and Guidance
Organizations ought to consider the following points:
- Providing adequate resources to the cybersecurity program to effectively support the organization’s IT and OT risk management strategy.
- Considering the complete life cycle of OT systems when formulating policies.
- Understanding and managing legal and regulatory cybersecurity requirements that impact OT operations.
- Designating one or more senior officials who hold responsibility and accountability for the governance and risk management of IT and OT cybersecurity programs within the organization.
- Establishing effective communication and coordination between IT and OT organizations.
- Cross-training IT and OT personnel to enhance their capabilities in supporting the cybersecurity program.
Risk Assessment
Conducting a cybersecurity risk assessment aims to identify potential risks and assess the potential impact on operations, assets, or individuals due to cyber incidents, which may include unauthorized access, use, disclosure, disruption, modification, or destruction of information systems or data. It is essential for organizations to carefully consider the frequency at which they update their risk assessments and test the effectiveness of their system cybersecurity controls.
OT-Specific Recommendations and Guidance
Within OT environments, risks and their impacts can extend beyond business and financial considerations to include safety, health, and environmental concerns. Consequently, conducting a cost-to-benefit analysis for certain types of risks may prove challenging. In such cases, organizations should consider examining historical incidents, both cyber and non-cyber, that have led to power loss, loss of control, disruption of upstream feed, reduction in downstream capacity, and significant equipment failures. By employing techniques like Process Hazard Analysis (PHA), Failure Mode and Effects Analysis (FMEA), or analyzing past events, organizations can gain insights into the potential consequences of a cyber incident. ISA 62443-3 provides valuable guidance for assessing cyber risks in environments where these consequences are possible.
When conducting risk assessments, it is crucial to identify vulnerabilities and threats specific to the OT environment. Maintaining an accurate inventory of IT and OT assets within the operational environment, including information such as product vendor, model numbers, firmware, operating systems, and software versions installed on the assets, facilitates the identification, tracking, and remediation of vulnerabilities.
To gather OT-specific vulnerability information, organizations can utilize various methods, such as monitoring security groups, associations, and vendors for security alerts and advisories. Detailed information about known vulnerabilities for hardware and software assets can be obtained from sources like the National Vulnerability Database (NVD).
Threat information relevant to the OT environment can be obtained from internal resources as well as external threat intelligence-sharing forums. Organizations should consider participating in cyber threat information-sharing initiatives to stay informed about emerging threats.
Risk Management Strategy
The risk management strategy serves as a guiding framework for framing, assessing, responding to, and monitoring risks, ensuring a consistent approach to risk-based decision-making throughout the organization. It encompasses the identification of risk tolerance, assumptions, constraints, priorities, and trade-offs to guide investment and operational decision-making processes. Furthermore, the risk management strategy outlines acceptable methodologies for risk assessment, potential risk response options, and establishes a continuous monitoring process to evaluate the organization’s security posture and the effectiveness of implemented security countermeasures and outcomes.
OT-Specific Recommendations and Guidance
When formulating an OT risk management strategy, organizations should take the following into account:
- Aligning the risk tolerance of the OT environment with the organization’s role in critical infrastructure and conducting sector-specific risk analysis.
- Documenting failure scenarios that involve IT components within the OT environment and comprehending their potential impact on operations and safety.
- Establishing processes for regularly updating information to assess the current risk posture of the environment and coordinating necessary adjustments to risk management and management controls.
Addressing both the likelihood and consequence of risks can contribute to the overall reduction of risk. In the context of OT systems, it is crucial for the risk management strategy to incorporate non-security and safety controls, such as pressure relief valves and manual valves. These controls play a role in mitigating the consequences of potential failures, further enhancing risk reduction measures.
Supply Chain Risk Management
Supply chains are intricate systems that rely on various business, economic, and technological factors. Organizations and consumers select suppliers and sources based on a multitude of considerations, ranging from corporate preferences and existing relationships to unique characteristics or limited supply availability.
Organizations are encouraged to explore the use of Software Bill of Materials (SBOMs) and distributed ledger technologies like blockchain to support supply chain risk management. SBOMs provide valuable information about software components and their dependencies, enabling organizations to determine if a device is affected by reported software vulnerabilities. Incorporating these technologies can enhance an organization’s ability to mitigate supply chain risks effectively.
OT-Specific Recommendations and Guidance
It is important for organizations to consider documenting and keeping track of serial numbers, checksums, digital certificates/signatures, or other identifying features that can help determine the authenticity of OT hardware, software, and firmware provided by vendors. Furthermore, organizations should assess whether the OT components are purchased directly from the original equipment manufacturer (OEM) or an authorized third-party distributor or reseller. Regular evaluation of suppliers is crucial to ensure their adherence to best practices.
Many OT components and devices rely on open-source libraries to support their functionality. It is necessary for organizations to identify the open-source dependencies associated with their OT components and establish a monitoring system for open-source information, such as vendor websites or cyber news sources, to stay informed about any disclosed vulnerabilities or counterfeits. Additionally, organizations may find it beneficial to consider utilizing an industry-recognized certification process for OT products, as it can support supply chain risk management efforts.
Next week we will continue with describing the Protect function of the NIST Cybersecurity Framework.





0 Comments