ENISA’s Threat Landscape Report 2022 – Part 5 – Social Engineering

Social engineering encompasses a wide range of activities that aim to exploit human errors or behaviour, with the ultimate goal of accessing information or services. It employs various forms of manipulation to deceive victims into either making errors or surrendering sensitive or confidential information. In cybersecurity, social engineering deceives users into opening documents, files, or emails, visiting websites, or granting unauthorized individuals access to systems or services. Despite the potential abuse of technology, these tactics are always dependent on human involvement for success.
The threat landscape is primarily composed of the following attack vectors: phishing, spear-phishing, whaling, smishing, vishing, business email compromise (BEC), fraud, impersonation, and counterfeiting.
Phishing is a fraudulent activity that aims to steal sensitive information, such as passwords and credit card numbers, through deceptive emails that use social engineering techniques.
Spear phishing is a more advanced version of phishing that targets specific organizations or individuals.
Whaling is a type of spear-phishing attack that targets high-level individuals such as executives and politicians.
Smishing is another threat that involves the gathering of financial or personal information through SMS messages.
Vishing is similar to phishing, but it involves the use of voice communication via phone calls, where attackers use social engineering techniques to extract sensitive information from their victims.
Business e-mail compromise (BEC) is a fraudulent and highly sophisticated scam that specifically targets businesses and organizations. In this scam, criminals use social engineering techniques to gain unauthorized access to an employee’s or executive’s e-mail account, with the aim of initiating fraudulent bank transfers or financial transactions.
Fraud refers to the deliberate misrepresentation or concealment of a crucial fact that the victim is supposed to rely on. Impersonation occurs when an entity wrongfully assumes the identity of another entity to gain benefits. Counterfeit is the fraudulent replication of something.
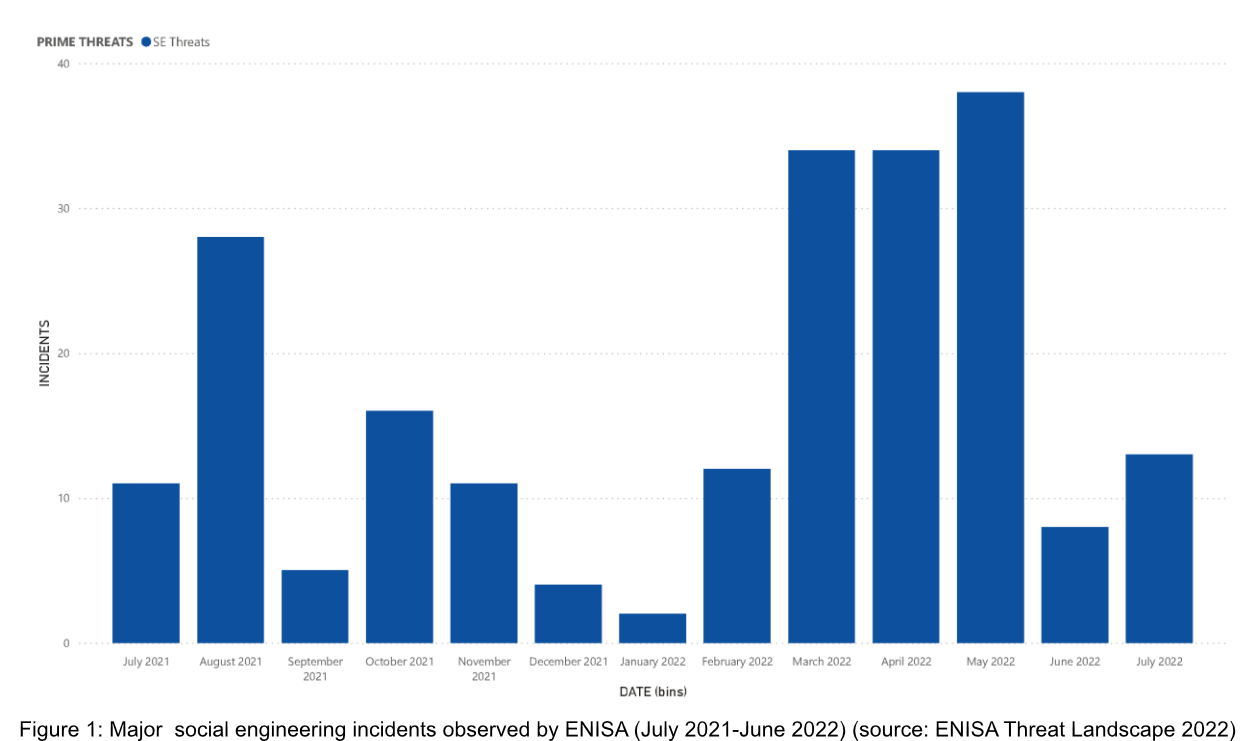
SOCIAL ENGINEERING TRENDS
Social engineering, particularly phishing, remains a prevalent tactic for malicious actors to carry out cyber-attacks. According to the Verizon Data Breach Investigations Report (DBIR), approximately 82% of breaches involve human error, with social engineering accounting for 60% of breaches in Europe, the Middle East, and Africa. The appeal of social engineering for attackers is clear: email is the most accessible means of reaching potential victims. Despite ongoing efforts to raise awareness, users still fall prey to these techniques. The DBIR notes that attackers often use stolen credentials to gather information from company emails to craft convincing pretexts for targeted attacks such as BEC scams.
Despite the takedown of Emotet in January 2021, malicious activities continued due to prolific phishing and fraud activity. In November 2021, Emotet resurfaced, reportedly at the behest of the Conti ransomware group. The playbook leak of this group highlighted that ransomware groups rely heavily on well-established social engineering methods such as spear phishing and phone calls for initial access and remain the primary vectors for payment fraud, increasing in both volume and sophistication. The cost of phishing attacks in 2021 has more than tripled since 2015, and the most time-consuming tasks to resolve these attacks include cleaning and fixing infected systems and conducting a forensic investigation.
Social engineering aims to gain access to information or services or to obtain knowledge on a specific subject, and it is also used for financial gain. Financial institutions were among the top organisations impersonated by phishers during the reporting period, followed by the technology sector with popular brands like Microsoft, Apple, and Google being the top impersonated targets. Social engineering campaigns also targeted popular cloud services used by remote workers and platforms used by streaming and media providers. Cybercriminals capitalized on the Covid-19 pandemic by using it as a theme for their social engineering campaigns.
Kits and services
Phishing attacks continue to be a significant threat to individuals and organisations alike, with criminals increasingly turning to ready-made material offered by phishing kits or Phishing-as-a-Service (PhaaS) to set up their social engineering campaigns. These services have become more sophisticated, with regional differences considered, filters applied to exclude unwelcome agents and obfuscation options added to the software-as-a-service package.
Phishing kits generally have a short lifespan, with almost one-third of deployed kits being used for no longer than a day. Microsoft reports that modern phishing kits are sufficiently sophisticated to masquerade as legitimate content, using spelling, grammar, and imagery that can fool even experienced users. Some kits contain added functionality that sends stolen credentials not only to phishers but also to the kit’s originating author or a sophisticated intermediary, exacerbating the impact of an incident on the victim.
Initial Access Brokers (IAB) are an extension of PhaaS, and this supply chain of social engineering specialists first opens the floodgates to an organisation before handing over access to follow-up actors. Criminal organisations demand easy access to organisations, leading to the growth of the IAB market. Professionalisation, diversification, and specialisation of threat groups mean that we are likely to see more cases of IABs fighting their way into an organization before making their access available for follow-up criminal activity.
The Dukes’ spear-phishing campaign
The recently discovered spear-phishing campaign by the espionage group The Dukes targeted various European diplomatic missions and Ministries of Foreign Affairs in October and November 2021. The approach used by The Dukes in this campaign was similar to their earlier attacks on French and Slovak organisations. The attackers impersonated government agencies and convinced their targets to open an HTML file, which downloaded a disk image (ISO or VHDX). This disk image contained further malware, eventually leading to a Cobalt Strike beacon. Disk images are a potent delivery method for malware as they evade SmartScreen and do not trigger any warnings for potentially unsafe files being opened.
A similar campaign was conducted in July 2021, where the initial email impersonated someone from the Belgian embassy in Ireland but did not contain any malicious content. Only after replying, victims received a follow-up email with a ZIP attachment containing a disk image (ISO) that led to a Cobalt Strike.
Attacks related to the war in Ukraine
In March 2022, a likely phishing campaign sponsored by a nation-state that targeted European government personnel responsible for managing logistics for refugees fleeing Ukraine was exposed. The campaign used the email account of a possibly compromised Ukrainian armed services member and employed an email with a subject line referencing a decision from the Ukrainian Security Council.
The number of threat actors using the war in Ukraine as a lure in phishing and malware campaigns has been steadily increasing. One of these campaigns, attributed to the Russian-based threat actor COLDRIVER, involved credential phishing emails aimed at government and defense officials, politicians, NGOs, think tanks, and journalists. COLDRIVER has previously targeted multiple Eastern European militaries and a NATO Centre of Excellence.
Another example is a phishing-based reconnaissance campaign in Europe by the Turla threat actor. Turla targeted the website of the Baltic Defense College and the Austrian Federal Economic Chamber in this campaign.
Given the types of cyberattacks that have already occurred in connection with the conflict in Ukraine, it is highly probable that similar social engineering attacks will occur in the future. These attacks will likely target European governments, civilians, and organizations, among other targets.
Phishing from known accounts
With the increase in the use of multi-factor authentication (MFA), attackers have shifted their tactics from targeting individual mailboxes to abusing legitimate infrastructure to carry out their operations. A notable example is the registration of trial tenants for services at Office 365, which makes the attacker’s email appear more legitimate. They may also compromise a Microsoft Exchange server using tactics such as ProxyShell or ProxyLogin to distribute phishing emails to internal and external accounts. In some cases, attackers even hijack mail conversations and modify replies to messages to increase their chances of success.
This trend is likely to continue as attackers look for ways to bypass MFA and exploit vulnerabilities in systems like Microsoft Exchange. The hijacking of mail conversations is also a common tactic in business email compromise (BEC) attacks.
Business e-mail compromise
The Business E-mail Compromise (BEC) is a highly financially impactful form of cybercrime. Unlike other types of cyberattacks, BEC attacks do not require multi-stage attacks or malware; rather, they rely on social engineering techniques, impersonation, and exploiting trust. As a result, attackers can execute financial transactions by simply asking for them. The median transaction size for BEC attacks has increased substantially, with only 41% involving phishing and about 25% using stolen credentials. Despite the efforts of law enforcement agencies, such as Interpol’s Operation Delilah, BEC attacks remain lucrative for criminals.
Malicious quick response (QR) codes
In January 2022, the FBI issued a warning about criminals utilizing QR codes to redirect victims to malicious websites that steal login and financial information. The Phishing Defense Center also observed a similar effort where threat actors targeted users of German banking by using malicious QR codes. It’s crucial to understand that these types of scams can occur both in the digital and physical realms.
Consent phishing
Microsoft and Mandiant have reported incidents of attackers using consent phishing to trick users into granting access and permissions to their applications and services. These threat actors create malicious applications in Azure or other platforms to gain persistent access to sensitive data and applications such as Exchange Online. By tricking non-privileged users to approve consent, the attackers obtain an access token and account-level access to the victim’s data without needing the user’s credentials.
While developing an app requires more technical skills and resources than subscribing to a phishing-as-a-service (PhaaS), this type of attack could still be valuable to threat groups due to its potential impact and lower chance of detection. Although it may not be the first choice for many attackers, the lack of visibility or knowledge by most organizations could increase the likelihood of consent phishing attacks.
Automation
Social engineering attacks are becoming increasingly automated as threat actors streamline their operations. While we don’t expect artificial intelligence to be driving phishing emails just yet, the growing automation of these attacks is a cause for concern.
In the near future, threat actors are likely to rely more heavily on customized, individualized, and personalized attacks. This will involve pulling victim information directly from published data breaches, as well as combining information from multiple data dumps. In addition, attackers are likely to use open-source information, such as social media profiles, personal and company websites, and published documents, to create more sophisticated attacks. These developments are expected to provide new opportunities for malicious actors to exploit their targets.
Smihisng via FluBot
FluBot is a prevalent mobile banking malware that mainly targets Android device users across Europe, utilizing SMS and MMS for distribution. The malware spreads through smishing messages that impersonate delivery companies, voicemail memos or fake software. These messages contain a link that directs the victim to a website, where they are instructed to download an app. Once downloaded, the app seeks permission to disable security features and access personal information. FluBot then propagates itself by sending phishing text messages to the victim’s contact list and collecting sensitive data such as credit card numbers, online banking credentials, and one-time passwords.
While iOS devices are not affected by FluBot, iPhone users are still vulnerable to traditional phishing sites and subscription scams if they follow the links in the SMS messages. In June 2022, a successful international law enforcement operation led to the takedown of FluBot. However, due to the malware’s lucrative potential, extensive target base, and ease of infection, it is highly likely that other criminal groups will attempt to fill the void in the mobile malware landscape.
Increase of attacks on crypto exchanges and cryptocurrencies owners
As cryptocurrencies continue to gain popularity, cybercriminals are increasingly targeting both cryptocurrency exchanges and individual owners of cryptocurrencies as their preferred choice of payment. This trend was demonstrated earlier in 2021 with the attacks on Coinbase users, and it’s likely that similar attacks will continue to occur in 2022.
Moreover, the non-fungible tokens (NFT) market has also become an area of interest for social engineering attacks by criminals, who employ methods similar to those used in “traditional” markets such as creating fake profiles on social media, hijacking social media accounts, creating counterfeit material (such as fake mints), phishing fraud, and impersonation attacks.
As cryptocurrencies and their derivatives become more popular, we can expect to see a corresponding increase in social engineering attacks targeting these phenomena.
Vishing using the safe account scams
The “safe account scam” has been identified as a new tactic being used in vishing. In this scam, attackers pose as a police officer or financial institution employee and convince victims that their bank account has been compromised. They then persuade the victim to transfer their funds to a so-called “safe account.” Unfortunately, this account is controlled by fraudsters, and victims soon discover that they have lost their life savings within minutes.
The number of vishing cases has also risen dramatically, increasing by 550% in the last year. This trend is expected to continue in the near future.





0 Comments