Defense in Depth strategies – Part 3

Risk Management as a Defense-in-Depth strategy element for ICS
Understanding the business risk associated with ICS cybersecurity and managing that risk is the first stop to improving the enterprise’s cybersecurity posture.
Indispensable in the application of a Defense in Depth layered cybersecurity approach is:
- a clear understanding of the threats to the business
- the operational processes and technology used within the organization
- its unique functional and technical requirements
Multitier Risk Management Integration
In order to integrate the ICS risk management process throughout the enterprise, a three-tiered approach should be deployed to address the risk at the following level
- Organisation (Tier 1)
- Mission / Business Processes (Tier 2)
- IT & ICS (Tier 3)
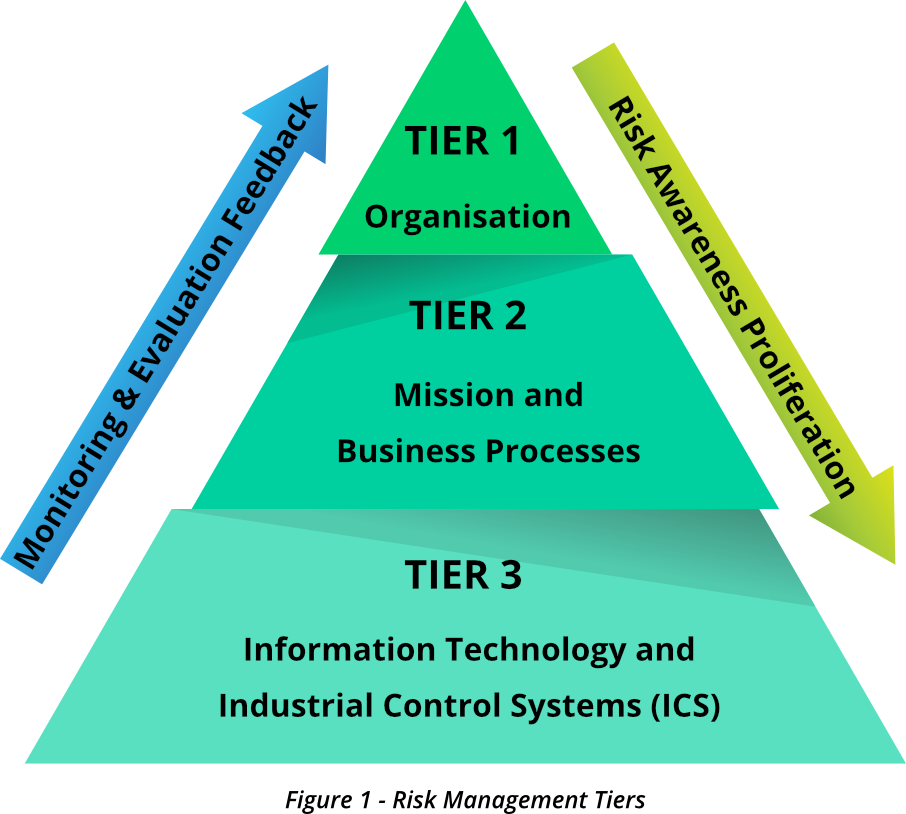
Tier 1
At this level, the enterprise addresses the risk from an organisational perspective starting with risk framing which provides the context for all risk management activities and the basis for risk management throughout the enterprise inclusive of the Operational Technology (OT) domain.
It determines:
- The techniques and methodologies used to evaluate information system-related security risks and other types of risk of concern from an overall business perspective,
- The techniques and strategies used to assess the significance of the risks identified during risk assessments,
- The nature and degree of risk mitigation measures applied to address identified risks,
- The level of risk the enterprise plans to accept (risk tolerance),
- How the enterprise plans to monitor risk day-to-day,
- The degree and type of oversight required to ensure that the risk management strategy is being successfully executed.
Tier 2
Addresses risk from a mission/business process perspective informed by the risk context, risk decisions, and risk activities at Tier 1.
It includes:
- Describing the underlying ICS functions and processes that support the enterprise,
- Listing and arranging the ICS functions and processes with respect to the overall goals and objectives of the enterprise,
- Defining the types of information required to successfully carry out the core ICS functions and processes and their interdependencies and information flows (information and security architecture),
- Developing an ICS information protection strategy and incorporating ICS security requirements into the operational processes,
- Identifying the level of autonomy with regard to assessing, evaluating, mitigating, accepting, and monitoring risk.
Tier 3
Implements security at the operational level and addresses risk from an information system perspective. The risk context, risk decisions, and risk activities at Tiers 1 and 2 guide activities at this level.
Tier 3 risk management activities include performing the five system-level ICS risk management functions
- identify
- protect
- detect
- respond
- recover
as part of a disciplined and structured system development life cycle process.
Managing risk at the ICS level does not require having risk management active on the higher tiers. Enterprises can manage risk at the ICS level only by applying risk management practices having defined a workable risk management process.





0 Comments