Network segmentation in protection of industrial control systems
In recent years, industrial control systems have repeatedly been the victim of cyberattacks. The multidimensional attack on Ukraine’s energy infrastructure deprived of energy of nearly 225,000 users. Can network segmentation help protect against an attack or reduce its effects?

Cyber attacks on industrial systems. Is the threat real?
Hacker attacks are an increasingly serious problem that can seriously threaten the functioning of factories or power networks. It should be noted that we are talking about specific, effective attacks, and not the incidents themselves. Let’s examine some of them:
- 2010 – Stuxnet – attack on uranium enrichment infrastructure in Iran using malicious software. The indirect target of the attack was the SCADA system and PLC controllers. Reports report that the consequence of these activities was a delay in the program.
- 2015 – a multidimensional attack BlackEnergy on Ukraine’s energy infrastructure. Adversaries used sophisticated methods of attack: they were able not only to switch individual circuit breakers on power substations, but also to modify the firmware of selected devices to thus affect hardware converters, such as serial – Ethernet gateways. The power supply interruptions affected 225 thousand users.
The first of the recommendations that were passed in the SANS document describing in detail the attack on the power infrastructure of Ukraine in 2015 and 2016 was to conduct appropriate segmentation of the network. The use of the correct division based on the reference model of network architecture – Purdue Model may contribute to delaying the finalization of an attack or to limiting its effects.
Network segmentation – what is it and how it can improve security
Network segmentation consists of isolating functional layers of devices and communication methods, which allows to limit the exchange of information between components of different layers to the necessary minimum.
The segmentation process is complicated by the fact that the target network design often changes during its implementation, which is why it may be useful to collect as much information as possible about devices working in the OT network.
In a frequently changing, extensive production environment, keeping project documentation up to date can also be a challenge. A list of devices and ports alone is not enough. Further data analysis is needed to obtain the right rules for active network devices separating individual layers.
Purdue Enterprise Reference Architecture (PERA) Model
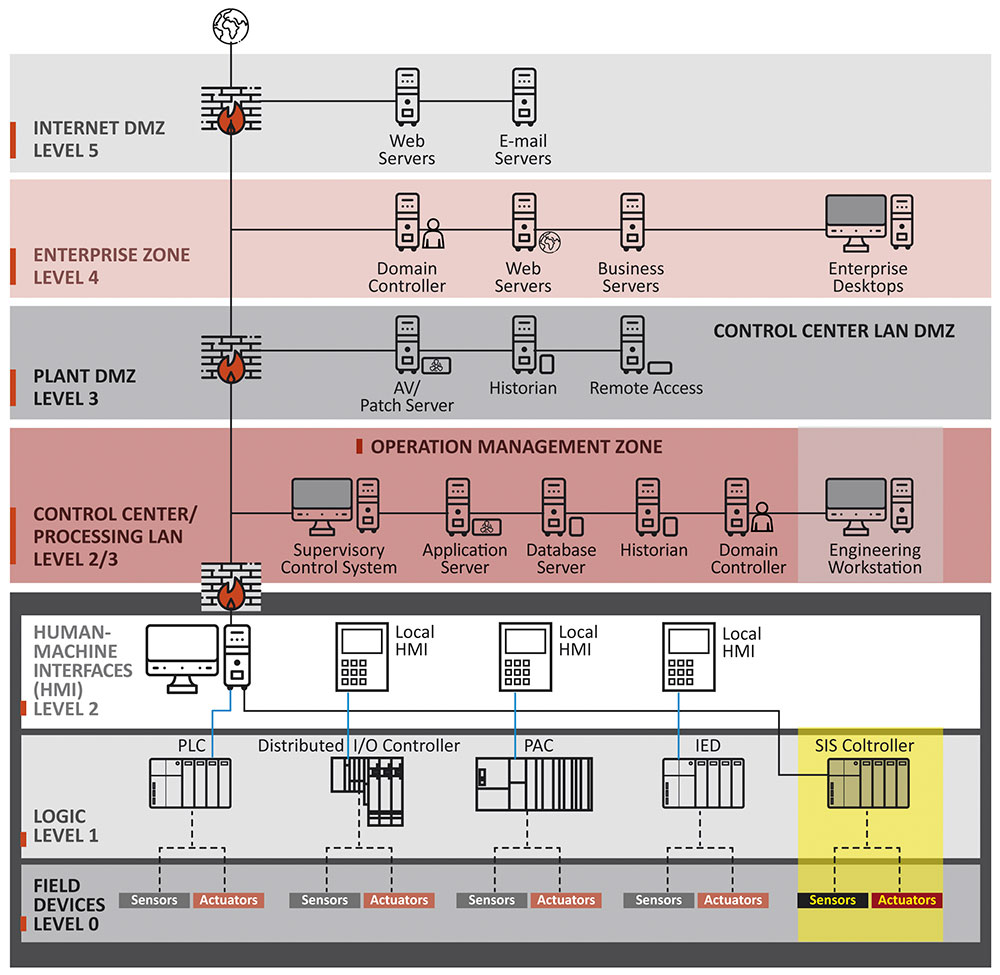
The need to integrate business services between enterprises (Business-To-Business interface, RSG, etc.), and thus the presence of external connections in the company’s infrastructure makes it necessary to assess the level of security and isolate key areas responsible for the process in which such security should be provided in a specific way. Insulation should be carried out in such a way that devices requiring a similar level of security are in the same or adjacent layer.
The boundaries between the zones should be the subject of special attention, the correctness of the rules should be updated and verified, and the traffic within individual layers, if possible, should be monitored and analyzed (IPS / IDS).
The purpose of appropriate separation of OT networks from the business layer and the Internet is to impede the access of potential adversaries to devices directly responsible for the continuity of the process.
The lower, non-business layers have a direct impact on human life as well as the continuity of the process, which is why ensuring security is particularly important. Access to devices from the Internet – the main source of attacks on OT’s industrial infrastructure.
Access to devices from the Internet – the main source of attacks on OT’s industrial infrastructure
According to reports of a leading anti-virus software manufacturer, in the second half of 2018, access to devices from the Internet was the main source of attacks on industrial infrastructure. They accounted for about 1/3 of all attacks carried out on these devices. These data did not include e-mail attacks such as phishing, whaling or spear phishing.
According to the data available on the portal shodan.io, as of the day of writing the article, nearly 11 thousand network devices of three leading manufacturers of automation systems were exposed to the Internet. Data from other foreign portals show that this number can be up to four times higher. If only a part of them could be successfully attacked, many countries and global corporations would have to face destabilization.
Lack of direct connection of the automation system to the Internet does not provide security
Although various industrial protocols are used in individual layers of OT industrial networks, their diversity alone does not provide cybersecurity. The lack of a direct connection between the automation controller and the Internet does not mean that it is not possible to connect to it from a computer in the internal network. It is worth knowing the reason for this problem.
There are two basic protocol families in industry: routable and non-routable. They differ in the scope and availability of the information provided.
Routable protocols can be used to exchange data and be transported to other layers through network devices such as routers or firewalls. Most often they use the IP layer of the ISO-OSI model (TCP / IP or UDP / IP).
For non-routable protocols, the devices limiting the range of information transfer are the previously mentioned active network devices. Initially used: Modbus RTU, Profibus DP, DNP3, IEC60870-5: 101 were supplemented with such protocols as: Modbus TCP, Profinet, DNP3 after TCP / UDP as well as IEC60870-5: 104.
Transferring information between networks belonging to different groups is possible not only by using a dedicated converter, but also by using optional communication modules for PLC controllers. The use of such solutions requires modification of the control program, but allows the transfer of information from one subnet to another, e.g. routable (Profinet) to non-routable (Profibus DP).
An example of an attack on the power grid of Ukraine shows that merely ensuring the diversity of protocols (routable and non-routable) does not mean that potential adversaries will not be able to threaten the critical infrastructure.
Examples of good practices in network segmentation:
Network segmentation cannot be a one-off activity, it should be understood as a process and ensure that rules or software on devices are up to date. Below is a list of good practices that can help protect against cyberattacks:
- applying the rule of minimum permissions and limiting stations and people having access to the lowest layers,
- cyclical update and verification of the correctness of the network rules of active devices enables proactive improvement of the security level,
- moving devices providing remote access outside the OT industrial network to higher layers – allows for proper management and limitation of access to devices to the necessary minimum. Adverse effects can be recorded or detected by tools such as IDS / IPS,
- For critical processes and security systems, solutions that provide physical separation, such as air-gap, may be considered.



0 Comments