
by Justyna Thiede | 10 May 2020 | Blog-EN
Michał Kwiatkowski Cloud computing is the foundation of many digital transformation projects. Currently, enterprises see progressively more value in the ability to scale the cloud environment, being able to transfer part of the responsibility for reliability onto a...

by Justyna Thiede | 9 April 2020 | Blog-EN
Łukasz Dudkowski Can Building Management Systems be Potential Attack Vectors for Industrial Control Systems? For many enterprises, working with advanced industrial systems the simultaneous implementation and use of Building Management Systems (BMS) is necessary....

by Justyna Thiede | 8 April 2020 | Blog-EN
Maciej Miszczyk QQBrowser is a web browser developed by Tencent. It is one of the most popular web browsers used in China. During our tests, we have found a vulnerability which allows an unprivileged local attacker to gain code execution as NT AUTHORITYSYSTEM....

by Justyna Thiede | 2 April 2020 | Blog-EN
Michał Stępień In factories, companies and enterprises, cybersecurity for IT and OT departments should not be treated as separate issues. Historically, OT engineers have treated IT as a necessary evil, some of them even would go as far as “locking the infrastructure...
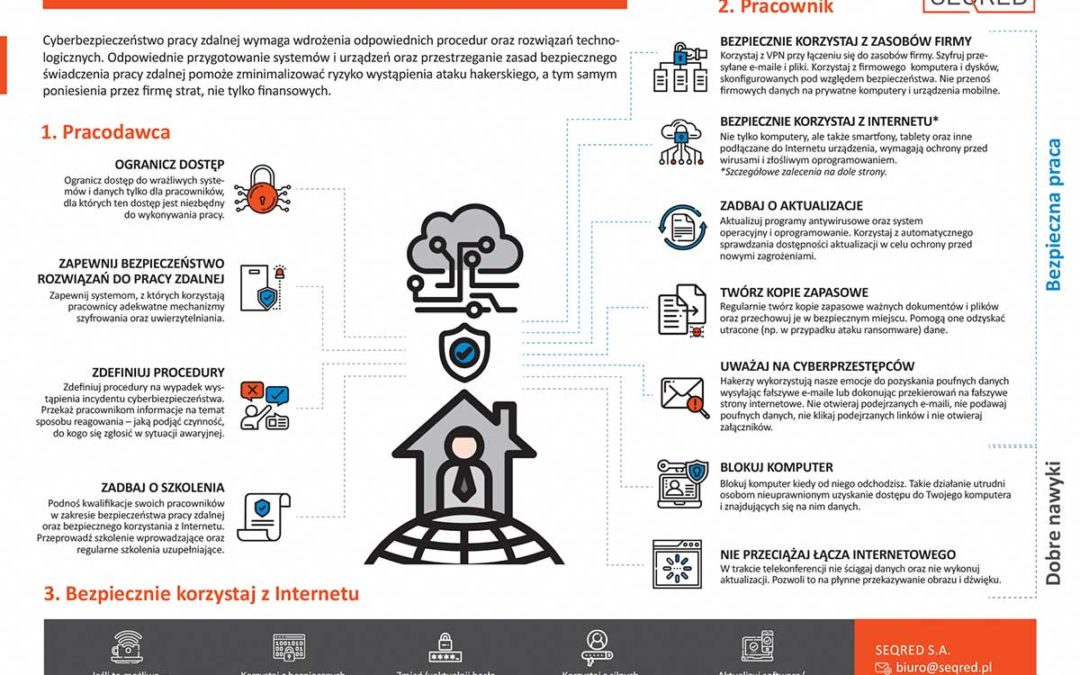
by Justyna Thiede | 26 March 2020 | Blog-EN
Seqred In order to ensure the cyber security of operations for staff working remotely it is vital to implement a number of appropriate procedures and technical measures. Adequate preparation of devices and systems used, as well as maintaining appropriate safety...






